Introduction:
In this guide we will see how to install and configure OpenLDAP as Policy Store.
Environment:
- Policy Server: R12.52SP1, R12.52SP2,R12.51
- Policy Store : OpenLDAP 2.4.4
Instructions
This guide will cover installing and configuring OpenLDAP as policy store right from the scratch.
So, for simpllicity, we will divide this into two broad category as follows.
- Install and run OpenLDAP
- Configure OpenLDAP as Policy store
Note : If you already have an working OpenLDAP instance ,you can skip step A.
A. Install and run OpenLDAP
- Download OpenLDAP version 2.4.x from OpenLDAP, Download
- Extract the openldap tar file
- [root@lodbl511vm027 OpenLDAP]# tar -xvzf ./openldap-2.4.44.tgz
- CD to the extracted folder
[root@lodbl511vm027 OpenLDAP]# cd openldap-2.4.44 - Execute configure command
[root@lodbl511vm027 OpenLDAP]#./configure - Compile the source by executing make command
[root@lodbl511vm027 OpenLDAP]# make - Install by executing make install command
[root@lodbl511vm027 OpenLDAP]# make install - Open slapd.conf file and modify the database directives as below :
suffix "dc=example,dc=com"
rootdn "cn=Manager,dc=example,dc=com"
(Note : you can choose any suffix domain of your choice. The default root DN password is secret )
- Start OpenLDAP server
- Create a file named rootsuffix.ldif with following content:
dn: dc=example,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
dc: example
o: ExmapleCo
(Note : The DN that you specify here need to match the suffix in the slapd.conf file)
- Import the rootsuffix.ldif file as below:
ldapadd -f ./rootsuffix.ldif -D "cn=Manager,dc=example,dc=com" -w secret
e.g.
[root@lodbl511vm027 OpenLDAP]# ldapadd -f ./rootsuffix.ldif -D "cn=Manager,dc=example,dc=com" -w secret
adding new entry "dc=example,dc=com"
- Test the LDAP connectivity by configuring OpenLDAP server details in the Policy Server Management Console(This can also be done using any other LDAP browser like JXPlorer )
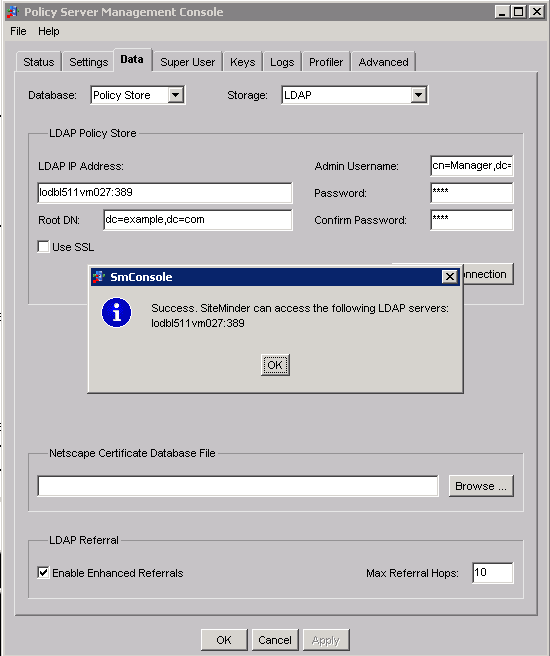
Few handy commands :
To start OpenLDAP:
[root@lodbl511vm027 openldap-2.4.44]# /usr/local/libexec/slapd
(Optional) Start OpenLDAP in debug mode :
To start OpenLDAP:
[root@lodbl511vm027 openldap-2.4.44]# /usr/local/libexec/slapd -d 1
To check if OpenLDAP is running :
[root@lodbl511vm027 openldap-2.4.44]# cat /usr/local/var/run/slapd.pid
30538
To Stop OpenLDAP:
kill -INT `cat /usr/local/var/run/slapd.pid`
Default OpenLDAP config file location : /usr/local/etc/openldap/slapd.conf
Default OpenLDAP schema folder location: /usr/local/etc/openldap/schema/
B. Configure OpenLDAP as Policy store
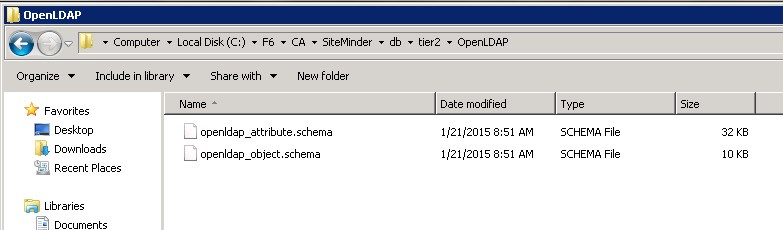
- Specify the CA Single Sign-on Schema Files
Navigate to <siteminder_home>/db/tier2/OpenLDAP and copy the following files to the schema folder in the OpenLDAP installation directory:
openldap_attribute.schema
openldap_object.schema
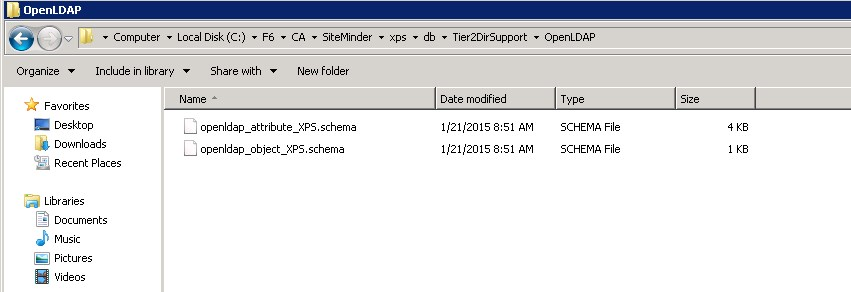
Navigate to <siteminder_home>/xps/db/Tier2DirSupport/OpenLDAP and copy the following files to the schema folder in the OpenLDAP installation directory:
openldap_attribute_XPS.schema
openldap_object_XPS.schema

Then, add the following entries in the include section of the slapd.conf file:
# Specify the CA Single Sign-on Schema Files - START
include /usr/local/etc/openldap/schema/openldap_attribute.schema
include /usr/local/etc/openldap/schema/openldap_object.schema
include /usr/local/etc/openldap/schema/openldap_attribute_XPS.schema
include /usr/local/etc/openldap/schema/openldap_object_XPS.schema
# Specify the CA Single Sign-on Schema Files - END
- Specify Policy Store Indexing
Locate the following lines:
# Indices to maintain
index objectClass eq
Insert a new line in the file, and then add the following lines:
#Specify Policy Store Indexing START
index smAdminOID4 pres,eq
index smAuthDirOID4 pres,eq
index smAzDirOID4 pres,eq
index smcertmapOID4 pres,eq
index smIsRadius4 pres,eq
index smIsAffiliate4 pres,eq
index smParentRealmOID4 pres,eq
index smPasswordPolicyOID4 pres,eq
index smAgentGroupOID4 pres,eq
index smKeyManagementOID4 pres,eq
index smAgentOID4 pres,eq
index smAgentKeyOID4 pres,eq
index smRootConfigOID4 pres,eq
index smAGAgents4 pres,eq
index smDomainAdminOIDs4 pres,eq
index smDomainOID4 pres,eq
index smvariableoid5 pres,eq
index smNestedVariableOIDs5 pres,eq
index smvariabletypeoid5 pres,eq
index smActiveExprOID5 pres,eq
index smDomainUDs4 pres,eq
index smVariableOIDs5 pres,eq
index smusractiveexproid5 pres,eq
index smPropertyOID5 pres,eq
index smPropertySectionOID5 pres,eq
index smPropertyCollectionOID5 pres,eq
index smFilterClass4 pres,eq
index smTaggedStringOID5 pres,eq
index smNoMatch5 pres,eq
index smTrustedHostOID5 pres,eq
index smIs4xTrustedHost5 pres,eq
index smDomainMode5 pres,eq
# index smImsEnvironmentOIDs5 pres,eq
index smSecretRolloverEnabled6 pres,eq
index smSecretGenTime6 pres,eq
index smSecretUsedTime6 pres,eq
index smSharedSecretPolicyOID6 pres,eq
index smFilterPath4 pres,eq
index smPolicyLinkOID4 pres,eq
index smIPAddress4 pres,eq
index smRealmOID4 pres,eq
index smSelfRegOID4 pres,eq
index smAzUserDirOID4 pres,eq
index smResourceType4 pres,eq
index smResponseAttrOID4 pres,eq
index smResponseGroupOID4 pres,eq
index smResponseOID4 pres,eq
index smRGResponses4 pres,eq
index smRGRules4 pres,eq
index smRuleGroupOID4 pres,eq
index smRuleOID4 pres,eq
index smSchemeOID4 pres,eq
index smisTemplate4 pres,eq
index smisUsedbyAdmin4 pres,eq
index smSchemeType4 pres,eq
index smUserDirectoryOID4 pres,eq
index smODBCQueryOID4 pres,eq
index smUserPolicyOID4 pres,eq
index smAgentTypeAttrOID4 pres,eq
index smAgentTypeOID4 pres,eq
index smAgentTyperfcid4 pres,eq
index smAgentTypeType4 pres,eq
index smAgentCommandOID4 pres,eq
index smTimeStamp4 pres,eq
index smServerCommandOID4 pres,eq
index smAuthAzMapOID4 pres,eq
index xpsParameter pres,eq
index xpsValue pres,eq
index xpsNumber pres,eq
index xpsCategory pres,eq
index xpsGUID pres,eq
index xpsSortKey pres,eq
index xpsIndexedObject pres,eq
#Specify Policy Store Indexing END
- Enable User Authentication
To enable user authentication add following:
# Enable User Authentication - START
access to attrs=userpassword by self write
access to attrs=userpassword by anonymous auth
access to attrs=userpassword by * none
# Enable User Authentication - END
- Support Client-Side Sorting
To support client side sorting add following:
# Support Client-Side Sorting - START
access to * by users read by anonymous read
sizelimit 500
allow bind_v2
# Support Client-Side Sorting - END
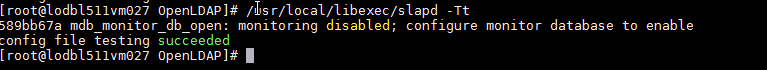
- Test the Configuration File
Run following command to test the slapd.conf file for any misconfiguration:
/usr/local/libexec/slapd -Tt
Run following command to index Database
slapindex -f /usr/local/etc/openldap/slapd.conf
- Start OpenLDAP server
- Create the Policy Store Database
Create a file named entities.ldif with following content:
#Netegrity, example.com
dn: ou=Netegrity,dc=example,dc=com
ou: Netegrity
objectClass: organizationalUnit
objectClass: top
# SiteMinder, Netegrity, example.com
dn: ou=SiteMinder,ou=Netegrity,dc=example,dc=com
ou: SiteMinder
objectClass: organizationalUnit
objectClass: top
# PolicySvr4, Netegrityr, CA, example.com
dn: ou=PolicySvr4,ou=SiteMinder,ou=Netegrity,dc=example,dc=com
ou: PolicySvr4
objectClass: organizationalUnit
objectClass: top
# XPS, policysvr4, siteminder, Netegrity, example.com
dn: ou=XPS,ou=PolicySvr4,ou=SiteMinder,ou=Netegrity,dc=example,dc=com
ou: XPS
objectClass: organizationalUnit
objectClass: top
Import the entities.ldif file as below:
ldapadd -f ./entities.ldif -D "cn=Manager,dc=example,dc=com" -w secret
e.g.
- Point the Policy Server to the Policy Store
Specify OpenLDAP server details and test the connectivity from Policy Server Management Console.

- Set the CA Single Sign-On Super User Password
Run following command:
smreg -su password
- Import the Policy Store Data Definitions
Run following command :
XPSDDInstall SmMaster.xdd
SmMaster.xdd is located at : <siteminder_home>\xps\dd folder
- Import the Default Policy Store Objects
Run following command:
XPSImport smpolicy.xml -npass
SmPolicy.xml is located at : <siteminder_home>\db folder
References:
- Installing an OpenLDAP server | Linux.com | The source for Linux information
- Configure OpenLDAP as a Policy Store - CA Single Sign-On - 12.52 SP1 - CA Technologies Documentation