The CA API Gateway can be configured to act as Service provider (SP), Identity Provider (IdP) or both. In this sample the Gateway is used as SP and the IdaaS platform onelogin.com is used as IdP. The communication is configured to use SAML 2.0. The sample are developed by Ben_Urbanski I think, see attached XML files.
First of all I set up the to service for SP and Idp in the gateway to work as designed.
- Create a "Publish Web API" as SP with custom resolution path as "/saml2/websso/serviceprovider"
- Import the policy SAML SSO ServiceProvider.xml into the above service.
- Create a "Publish Web API" as IdP with custom resolution path as "/saml2/websso/identityprovider"
- Import the policy SAML SSO IdentityProvider.xml into the above service.
- Check it is working with the URL "http://explore.apim.ca:8080//saml2/websso/serviceprovider" in your browser
- You should be redirected to a login page on the gateway.
To move the example to onelogin, you have to setup onelogin first.
For the test I received a onelogin domain with the name "catest.onelogin.com" The admin user which is used to
administer the domain is "steffen.miller@ca.com".
1. Create a new user e.g. "steffen@catest.com" in the tab "Users". It is important to create the user with the right domain, here "catest.com"
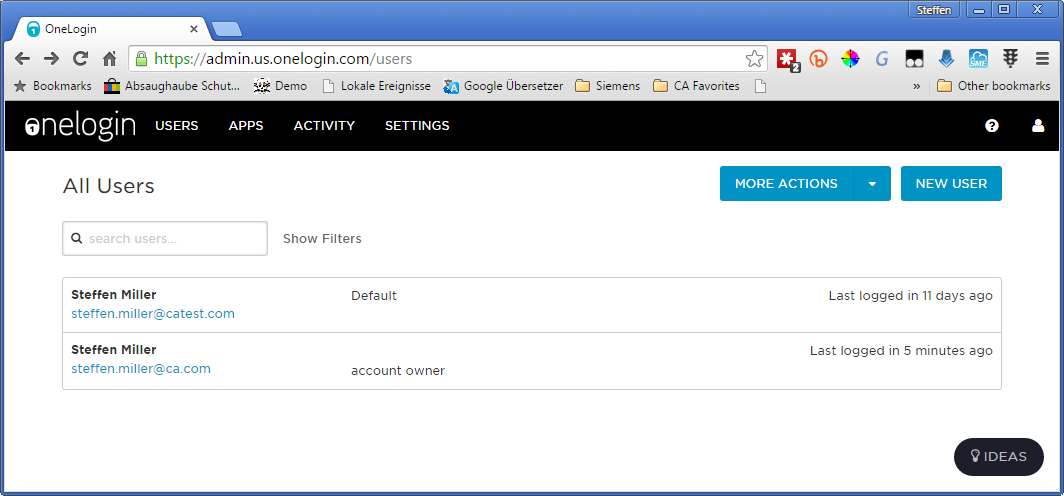
2. Check the user is added to the "default" role. If there is not default role, create one adn add the user to it.
3. Add a new app of type "OneLogin SAML Test (IdP w/ attr)"

4.Insert ServiceProvider (SP) information

5. In the SSO tab you can find the information needed for the SAML setup in the SP.

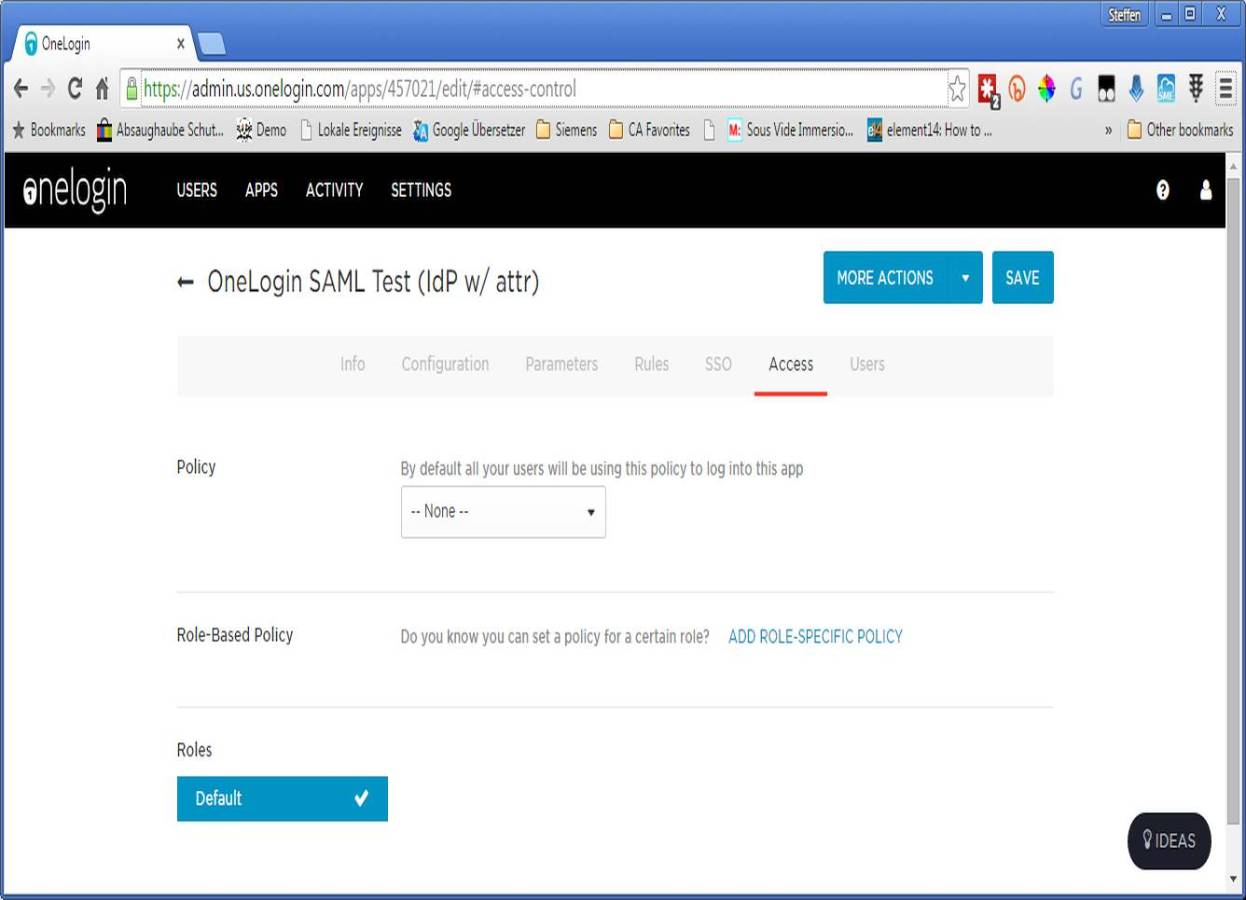
6. In the access tab you have to add the "Default" role to allow all users in this role access to that app.
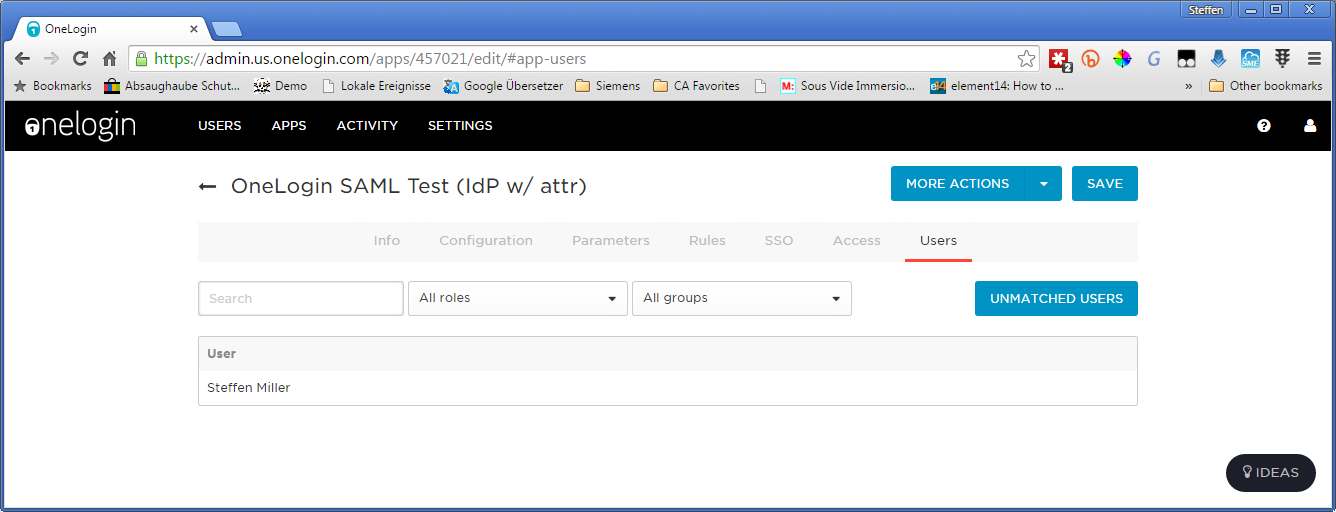
7. In the users app, check if your test user is shown
8. Now we have to change the SP on the gateway to use onelogin as idp. Therefor open the SP in the Policy Manager
and got to line 44 "Build SAML Protocol request" and open the wizard.


9. Set the entries according to the following images


10. Insert the "SAML 2.0 Endpoint (HTTP)" from onelogin to the destination field

11. Leave the fields 4 to 8 unchanged. And change the Recipient to "Issuer URL" from Onelogin

12. In the SP change the following lines:
34. deactivate
35. set identityProviderURL to "https://catest.onelogin.com/trust/saml2/http-post/sso/457021" as in the Onelogin "SAML 2.0 Endpoint (HTTP)" field.
13. Test the setup with "http://explore.apim.ca:8080/saml2/websso/serviceprovider", you should be redirected to

14. With successful login, you should be redirected to
