CA PAM online documentation includes the following page explaining how to set up CA PAM as a SAML Service Provider:
https://docops.ca.com/ca-privileged-access-manager/2-8-2/EN/implementing/configure-your-server/authentication/saml/act-as-a-service-provider-sp
One implementation integrating CA PAM with CA Single Sign-On is documented at
https://communities.ca.com/community/ca-security/ca-privileged-access-management/blog/2017/04/12/tech-tip-ca-privileged-access-manager-use-ca-single-sign-on-as-identity-authentication-to-ca-pam
Here we want to provide more information on the "Allow Just In Time Provisioning" option available in the remote SAML Identity Providers configuration:
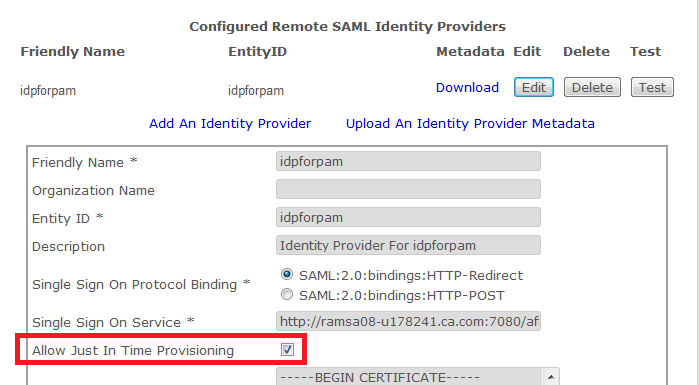
Just In Time Provisioning in this context means that when a user logs on to CA PAM for the very first time by clicking on the “Single Sign-On” link on the logon page, CA PAM will automatically create a user entry based on the information found in the assertion returned by the SAML Identity Provider assuming these conditions are met:
- The Allow Just In Time Provisioning checkbox is checked in the IdP configuration.
- Aside from the user name, the assertion needs to include the following attributes: firstName, lastName, e-mail, userGroup.
- A user group needs to exist in CA PAM already with a group name that matches the “userGroup” attribute of the user to be added.
You can verify that the required attributes are sent by your SAML IdP by using the test button on the Config > Security page for the SAML IdP integration:

When you click the button and provide the SAML user credentials, you will get a new tab showing the SAML SSO test response:

The “First Name” attribute it not labeled as "required" above, but it is. The test itself in fact will not add the user if it doesn’t exist yet. At the bottom of the response the decrypted SAML assertion is shown including the attributes:
…
</ns2:AuthnStatement>
<ns2:AttributeStatement>
<ns2:Attribute Name="firstName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<ns2:AttributeValue>pam</ns2:AttributeValue>
</ns2:Attribute>
<ns2:Attribute Name="lastName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<ns2:AttributeValue>User</ns2:AttributeValue>
</ns2:Attribute>
<ns2:Attribute Name="e-mail" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<ns2:AttributeValue>ed.vogel@ca.com</ns2:AttributeValue>
</ns2:Attribute>
<ns2:Attribute Name="userGroup" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<ns2:AttributeValue>SAML</ns2:AttributeValue>
</ns2:Attribute>
</ns2:AttributeStatement>
</ns2:Assertion>
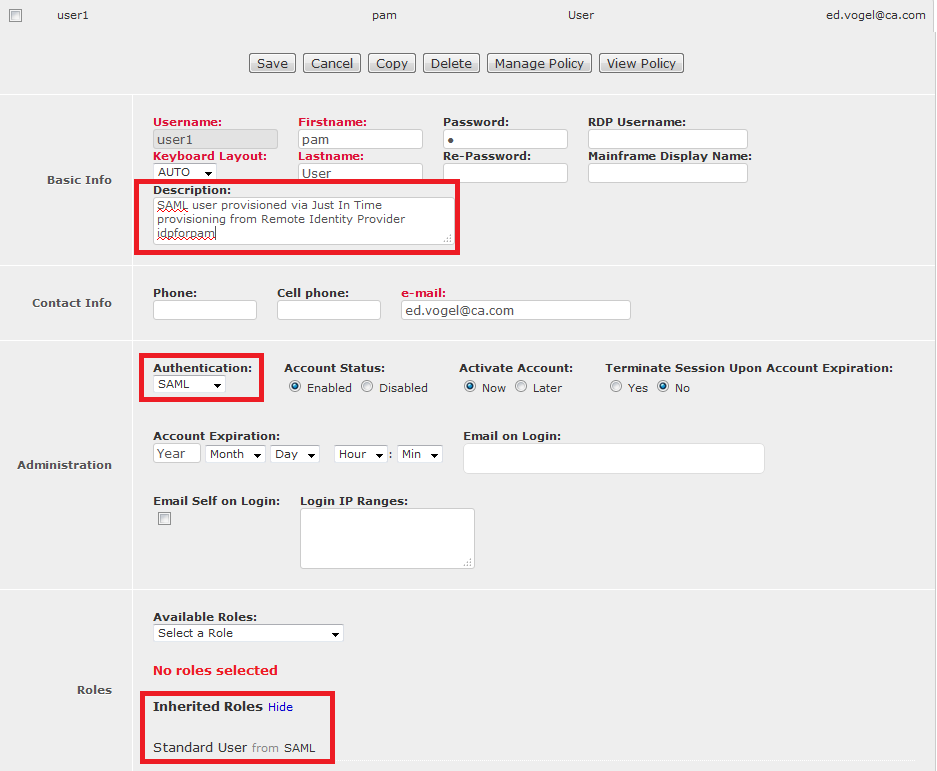
In this case the user group name is “SAML”. The user will be added to the existing user group named SAML in CA PAM and inherit the roles defined for that group. As mentioned above, the user group is not being created by JIT, it has to be created by the CA PAM Administrator, or via API calls, upfront and be assigned the role that SAML users in that group should inherit. In our case the group is defined with role “Standard User”.

The user created by JIT will inherit this role.