There are a couple of ways to integrate AWS with PAM. First of all, you may deploy PAM as an Amazon Machine Instance (AMI). Whether you do that or have a physical or VMware instance of PAM you may configure PAM to manage devices deployed in PAM. If you wish to deploy PAM in AWS you should review Technical Document TEC1536876. This article will focus on the second part, configuring PAM to manage devices that have been deployed in your AWS account.
The starting point for this is in AWS. You must have the credential for an AWS user that has permission to manage the AWS environment.
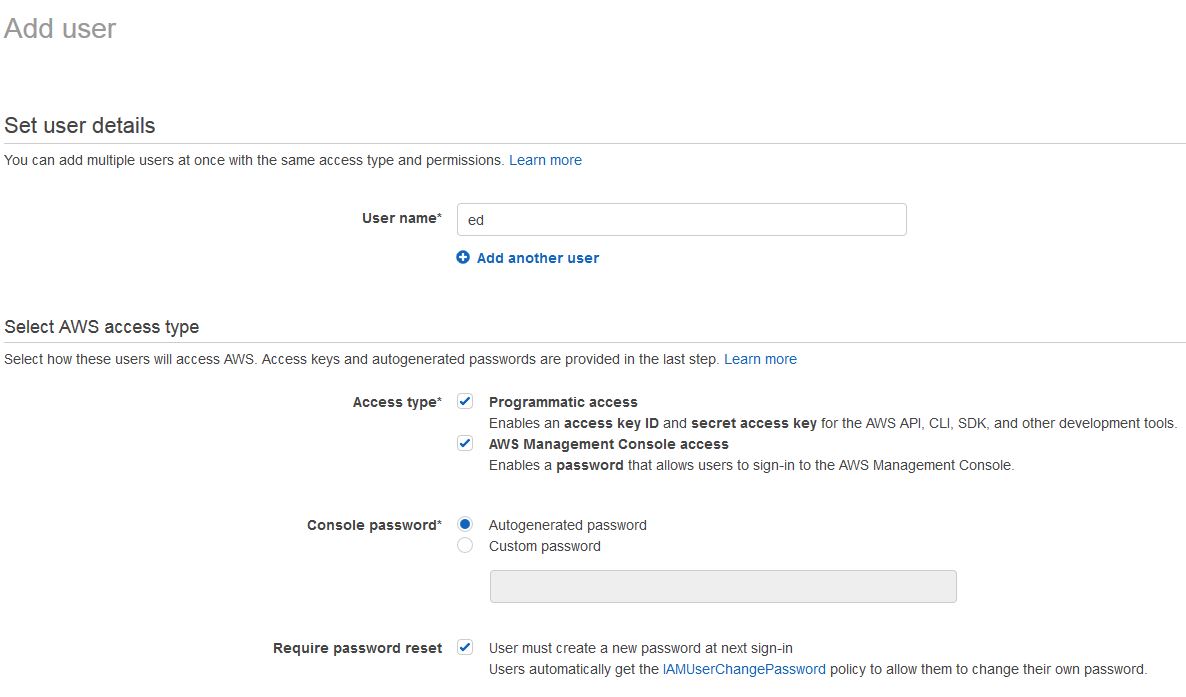
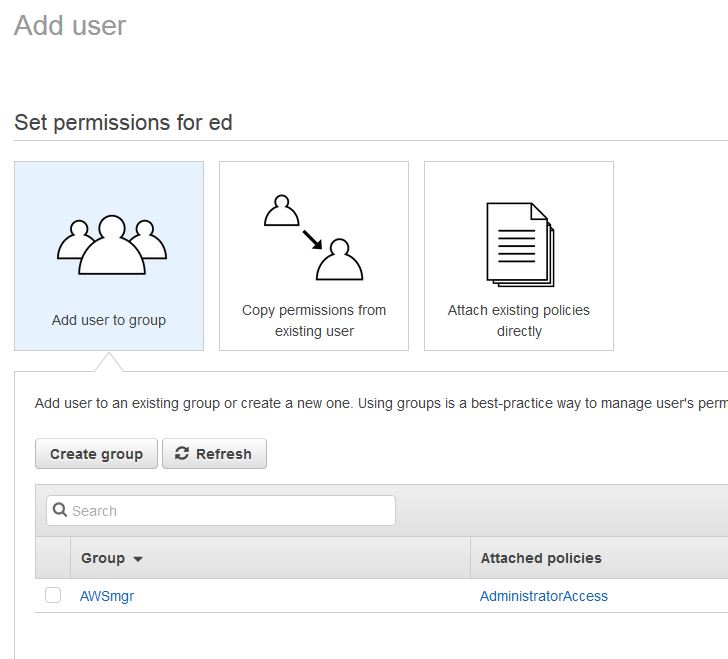
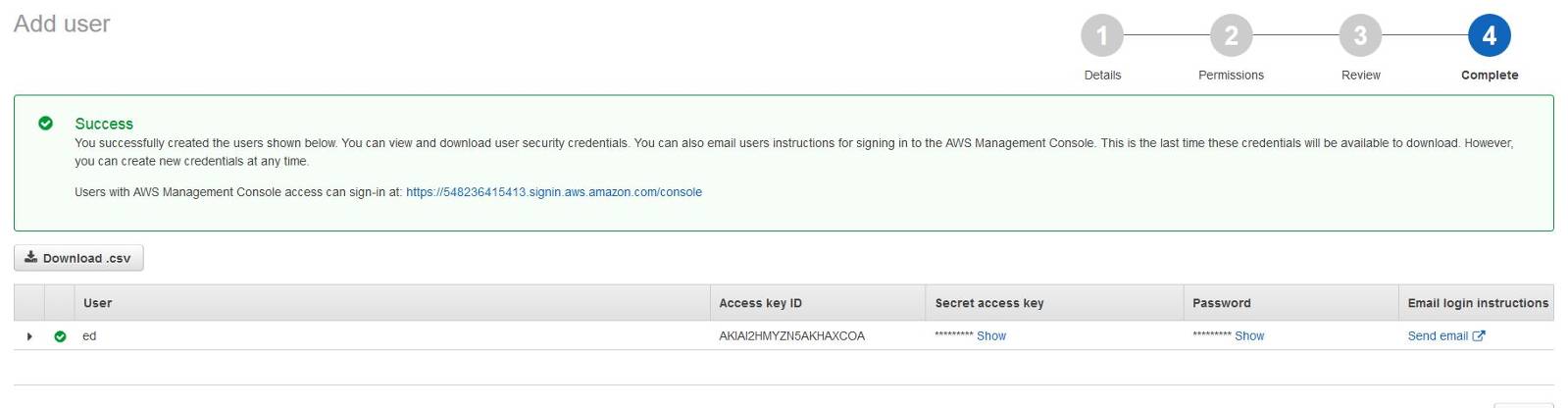
Once the user is created and has the right permissions you have to get the credentials to configure into PAM, specifically the Access Key ID and the Secret Access Key.
You will configure a Target Account in PAM. The Target Application already exists, provided your system has been licensed for AWS. When you configure the Target Account you must supply a few fields; User Friendly Account Name, Access Key ID, and Secret Access Key. You will have to select the Cloud Type. Usually this is Commercial, but you will have to change this to Gov Cloud, if you are configuring a Gov Cloud account. Clicking the lower magnifying lens icon will enable you to select AWS Access Credential Accounts, which will also cause the field above to be filled in. It's a good idea to select "Update both", as you will get confirmation that your credentials work.
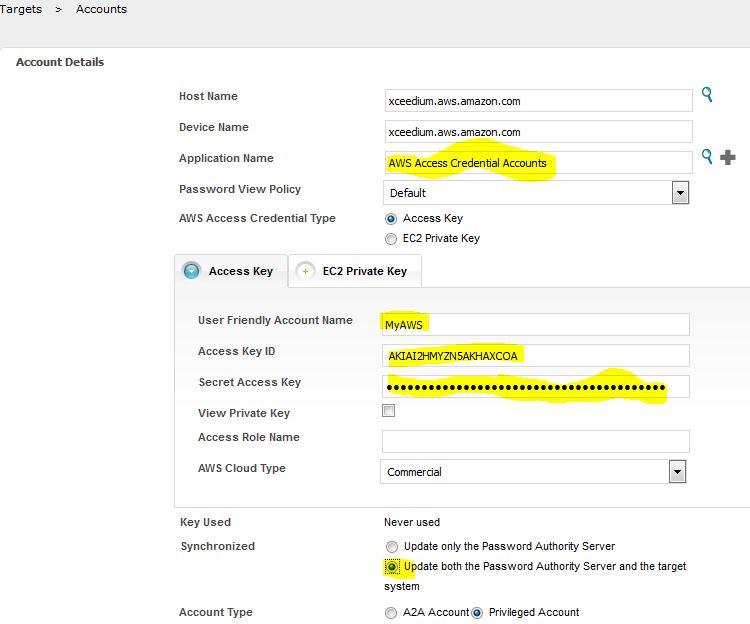
Once you have your credentials configured, you have to configure AWS on the 3rd Party page.
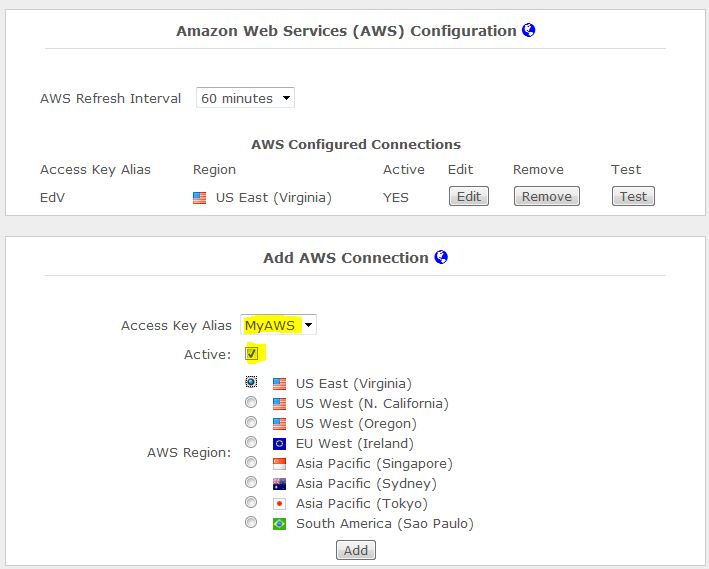
Select the User Friendly Account Name you configured in the previous step, as your Access Key Alias. Check the Active box and select the region you desire to manage. This will cause all active devices in that region to be imported into PAM. You can control what devices are imported and what they look like in PAM.
As soon as your AWS connection is configured PAM will begin importing the devices in the region. You can see some examples below.
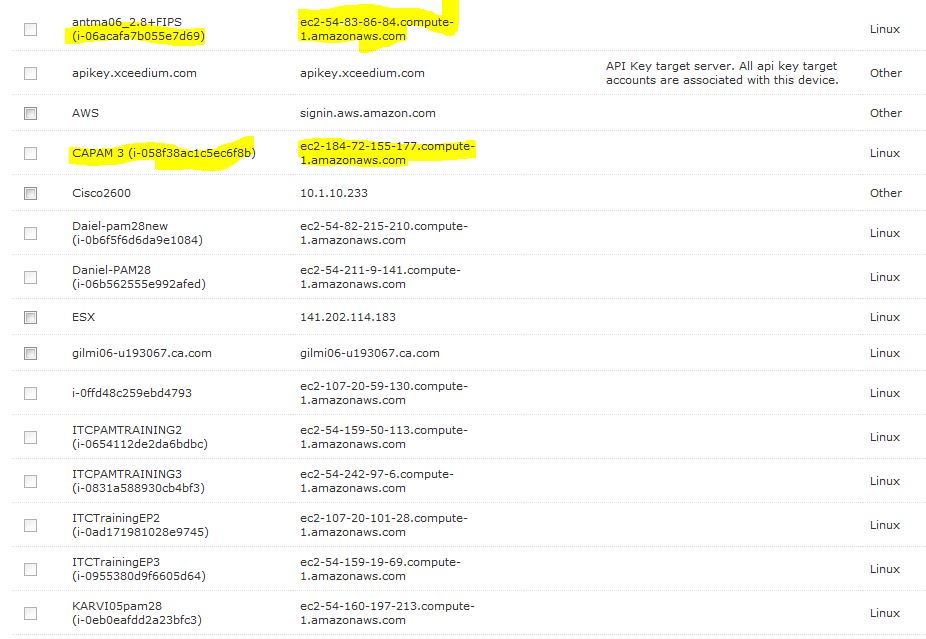
Devices configured with an XsuiteIgnore tag in AWS and those that are not active will not be imported. You can also configure XsuiteGroup tags, which will be used to put an imported device into an AWS group configured in PAM. This will simplify providing the right type of access to devices you add in AWS. Once you have added such a group, and created a Policy using it, you merely have to tag a new device with that Group name and users will have access to it the next time an AWS Device Import is performed. Read this article, Tech Tip - Using the Override Address Option for Devices Imported from AWS, if you wish to know how you may override the name and address imported from AWS. After the devices are imported they may be used in the same way as a physical device you have entered manually.
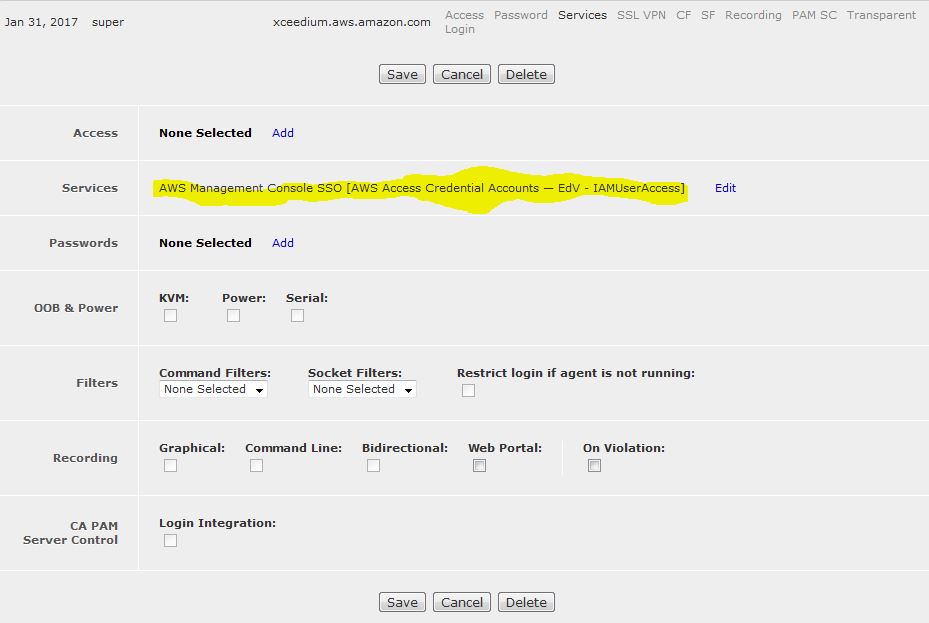
In addition to managing devices, you may wish to use the AWS Console from within PAM. To do this you must configure the appropriate Policy, to use the AWS Credentials. Below, you can see the Target Account, configured into Password Management, and the AWS Policy(IAMUserAccess) being used. Replace this with your credentials and policy.
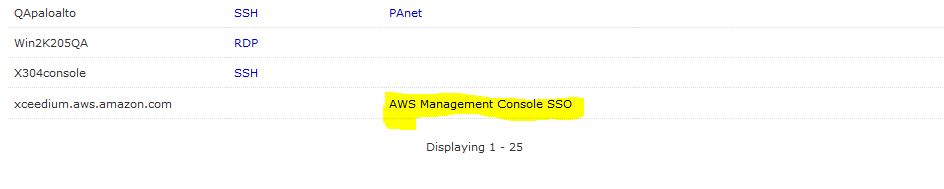
After you configure this Policy, you will see the AWS Management Console SSO link. If you configured only one set of credentials, as above, you will be taken right into the Management Console. If you configure multiple credentials you will have to select the one you wish to use.
If you still have any questions after reading this article please open a Support Ticket.