Deploy #microgateway in #openshift
Introduction
I am collating my recent PoC experience, where I had to prove the deployment of Microgateway in an Openshift environment and integrating the same with other cohort applications running as a separate project within OpenShift and also to edge gateway running outside Openshift environment
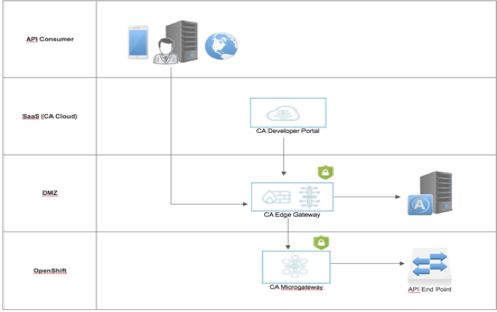
This document focuses only on configuring OpenShift and deploying Microgateway for an existing AMI instance, it also considers Docker setup since this will be pre-requisite for Openshift and provides a recommendation on AMI instance.
OpenShift Installation steps
Choose m5.xlarge AMI image in EC2 as OpenShift requires lot of resources for auto scalling etc., you may choose to go small and disable those features as well.
Once the image is launched and running, using your AWS key try to login to your instance with following command.
ssh -i <your key pair file>.pem ec2-user@<your instance Public DNS>.compute-1.amazonaws.com
Install Docker and add ec2-user to docker using following commands
sudo yum install docker
sudo usermod -aG docker ec2-user
Exit SSH and log back into your ec2 instance and start the docker.
sudo service docker start
after docker start you should be able to test Docker with this command to confirm docker is running.
docker ps
Once confirmed, now you may proceed to OpenShift installation steps.
Try downloading latest Openshift from github
Get Openshift from Github https://github.com/openshift/origin/releases
Using WGET command get the relevant release as needed for your endeavor.
wget https://github.com/openshift/origin/releases/download/v3.6.0-alpha.0/openshift-origin-client-tools-v3.6.0-alpha.0-0343989-linux-64bit.tar.gz
Untar the file and copy oc command as suggested below.
tar -xvzf openshift-origin-client-tools-v3.6.0-alpha.0–0343989-linux-64bit.tar.gz
sudo cp oc /usr/local/bin/
I had to add insecure registry to docker configuration as follows
cd /etc/sysconfig/
Add option--insecure-registry 172.30.0.0/16 to ‘docker’ file
Note: 172.30.0.0/16 – is your AWS subnet
It should look like this line below:
OPTIONS="--default-ulimit nofile=1024:4096 --insecure-registry 172.30.0.0/16"
Now restart your docker again using this command below
service docker restart
Once Docker is up and running you may proceed to start Openshift using following command:
oc cluster up --routing-suffix=<<Your IPV4 PUBLIC IP>>.nip.io --public-hostname=<<Public DNS IPV4>> --host-pv-dir=/var/tmp/openshift
Note: the highlighted entries should be changed as per your environment.
Post this command, you should receive this response below:
OpenShift server started.
The server is accessible via web console at:
https://<<your public DNS IPV4>>:8443
You are logged in as:
User: developer
Password: developer
To login as administrator:
oc login -u system:admin
You may launch the web console by following the url provided above and login using the administrator credentials (see above) to confirm OpenShift is up & running.

##
Deploying Microgateway inside Openshift
Using SSH login into your ec2 instance and create a folder, copy the enclosed zip file (Microgateway-Openshift.zip) into that folder. After unzip, you should see deployment.sh file along with .env and.yml files. Complete list is given below:
msgw-with-consul.env
deploy-with-consul.sh
msgw-with-consul.yml
msgw-secrets-with-consul.yml
msgw-with-consul.env – Contains all required environment variables including consul and microgateway version and tag information, you also have option to load OTK server host, port & certificate hear as needed.
msgw-with-consul.yml -- Contains the information regarding services, routes, templates, config maps and other variable declaration and association. Any 3rd party or edge gateway certificate can be bootstrapped through this file. Also if you need to connect outside cohort (Openshift), then declaration of IP, port and routes can be done through this file. Please refer some example as needed.
msgw-secrets-with-consul.yml – contains gateways credentials, key information, you may change the credentials as needed for your poc using this file.
Deploy-with-consul.sh – Will create an empty project and will associate the application and other configuration by utilizing the .yml & .env files described above.
After successful execution of this scripts, you should be seeing two pods both consul and microgateway running in the web console. Using routes declared earlier you may connect with relevant policy manager or start loading services and bundles into the gateway for your PoC.
My scripts were tested well in following environment:
- OpenShift Master: v3.6.1+008f2d5
- Kubernetes Master: v1.6.1+5115d708d7
- Docker: 17.06.2-ce
- Microgateway v1.0
Please amend the scripts as needed based on latest product versions.