Hi Sanjay,
I think there is fundamental misunderstanding here.
CA SSO supports two kinds of password policies :
1. Basic password policy - this is configured from Admin UI
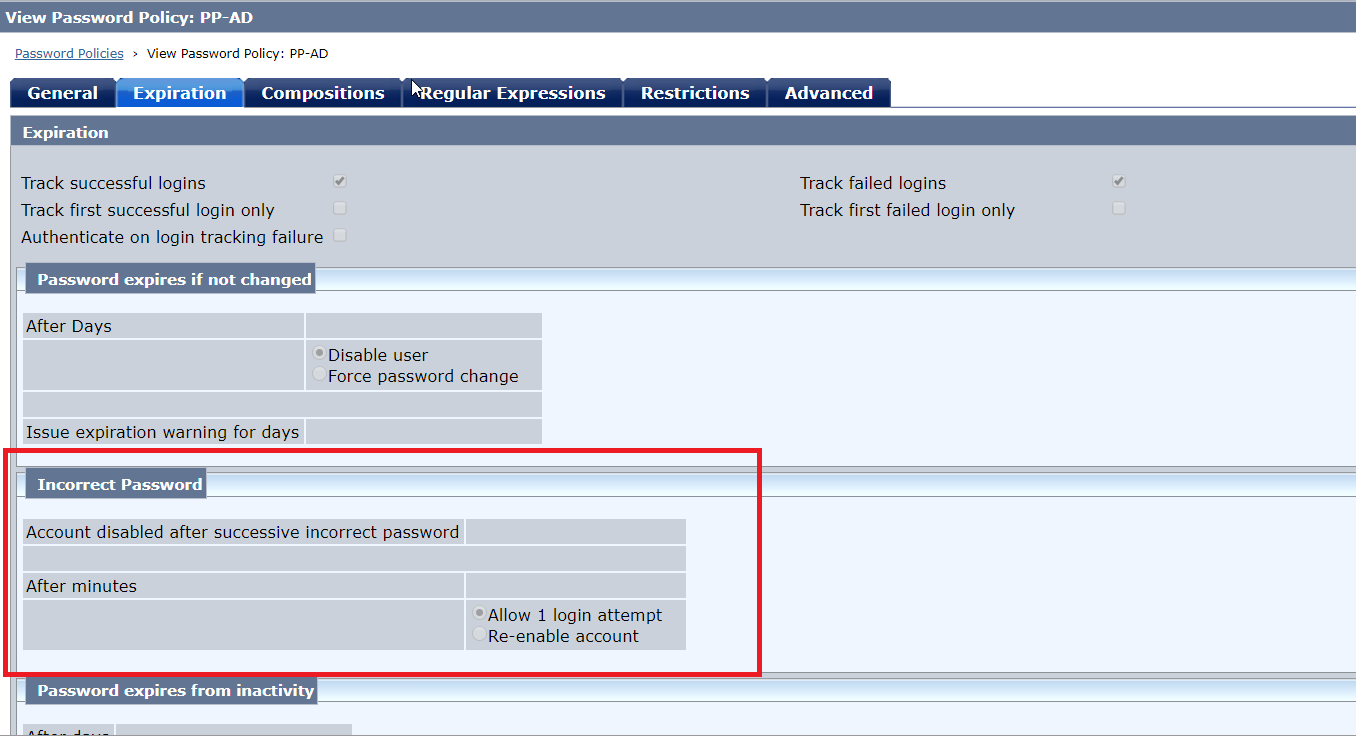
2. Advanced Password policy - this is configured using APS.cfg
These two are mutually exclusive configuration and only one can be enabled at anytime otherwise it may lead to inconsistencies.
Unless you have any specific need which BPS can't fulfill I would advise to stick to BPS as it provided more flexibility.
If you decide to go with BPS then you will need to disable APS which you can do so by following this guide :
How to disable APS ?
For APS, the maximum failure count (max login attempt with invalid password) can be configured in APS.cfg as:
#######################################################################
## "n" strikes processing
#######################################################################
##FAILURE COUNT##
///////////////////////////////////////////////////////////////////////
// The maximum consecutive password failures ("n" strikes and you're
// out). This value can be zero, or 3-9 inclusive. The recommended
// setting is 5. This setting is *separate* from the SMRETRY setting
// supported on SiteMinder authentication forms. Please see the APS
// documentation for details.
//
// This affects failures both on login and change password (change
// password only if Max Failures On Change is not set).
//
// This setting supports overrides.
///////////////////////////////////////////////////////////////////////
;;Max Failures=3
///////////////////////////////////////////////////////////////////////
// The maximum consecutive password failures ("n" strikes and you're
// out) to be used FOR PASSWORD CHANGES ONLY. This value can be zero,
// or 3-9 inclusive. The recommended setting is 5. If not set or zero,
// the setting for Max Failures (above) will be used.
//
// This setting supports overrides.
///////////////////////////////////////////////////////////////////////
;;Max Failures On Change=5
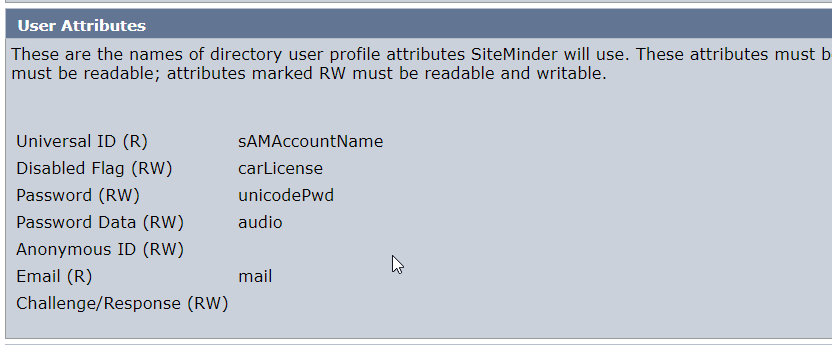
BPS doesn't use any of those smapsXXX attribute in user store instead it uses the user attributes as defined in the user directory configuration , particularly following so ensure that they are mapped to a valid attribute from user store:
- Disabled Flag
- Password Data ( This needs to be binary attribute )
Let me know if any question.
Regards,
Ujwol