Hi Ujwol,
we completed our production key store cleanup last saturday and it's successful. The reason for cleaning up our keystore is, we are having an integration in between CA API Gateway and CA SiteMinder policy server via Layer -7 agent.After the CA API Gateway upgraded from version 9.1 to 9.3 they are seeing the following errors more frequently.
20180430 07:48:29.907 | WARNING | | 10102 | CA Single Sign-On Authenticate Against CA Single Sign-On assertion: Unable to authenticate user using SSO Token:VSzzUIKgjyozGUoIabW0jtEEnSPVD6lTst77pRgJBjzJLryj6pCUAJhRiVugOp3WE6HNLRGjqYOhLtguanYwvbbSw8BMVusf8liF9JrqAfsIFs3/51CEDj5WRWg/S8a3OFG5hBfmHvUB/dJV6t2e1rYI2B52Cj7+i+GYqq9MH2KAjvVRujq+1+GurcdNhP27kXvqi8QltEN700kDNuhIj57lz/SghlOtXMknX5u1fLM9D+mGKmKdKD2Rt3ubTg2/LP4v7c0EV6kEXmXGNyd9Faw6LHTZyRKzJW/1iew4SGHpgReWi5eJFFSlwd970Gb5wyhMC3kCC/jZxSXFaqkk41sDAM76kKp3JzDyFV6CxOlBh2NpufSgnVS8oiKDcUDTIwMxKq0nZ3E2f3WWOKXbPSVnYd9s2rq6fEFA/xADzwoT4t39sPf/E4YqYf+aWy2Ar+kdQRsQ42FRe8uvX8tLoN00/5FckIdf7lb2YX53WJQBoM+55mmU6ziFrRqYFfTTbDBLXjRkrJ6I2b9R+W6uk+08fXSaxMuES3+1+0nSWxcw2pMu2G68+fG5IZJ/rhqycXReDmXjwO6xTvuU30qiOSq+2TZirankTICd3XfrlP0Pq5lDaFSP7ngDik/uNZw/oZQ+sVR3EfW9aDf/fxR7qff4GkyoirbAYE1+2pr7hpl5tUEFM7suNGdmYgxtBngNTf46yGzF4vrrq8Lp9X7kdB/hPqG63dIFKRWMSdHGXfmd4k7MPt+1f/GM4Ppztwr6cmhbe+Z3lh1iLa9cEIc/GKF3/8S3BZJut+aeX2DJkK7B2s4+sM74mAri6tdaMjyaoTlsCYV9sta89R0t0x9FxF/D16z3cKFshcX27rzGlSzlp4r9JKHdXfbeHSNauBFjEjpHrCtrVoh8LUONPIlKFsmXjW6x6vaCqa91+r7+yVwP3sVXoxPvdJaRWT2tNwnVJXqv77vIOAsa87v4vHXqPlFRzVTZ0sWNMmQWoVEbzTaxb294cFkvzN3ayGEYF9QokwU1ZwpKZQunn4k9rCsRekeakP0jPH1vYa61NczPskWyyAK6vMlZbwFPuTvfA68JliBPro5QZSaTIC0t4ewbbnqKaqRzJd1Bq8bvsJYvWrVZIN0EeC2CaO8sMJethS1OC/SnyfofvnZG71bEy+Yxdz8DRZ6Kn9UbH/zZ6mg+KmUkuV24dxLi39ZOZxMbAN6n8lIwI2C8DmxHSRdnh/SCBGbwipxfoD7G |
After i open a support ticket with CA, Support Engineer identified additional keys in our keystore and suggested to clean up the keystore to see if that resolves the issue. But even after the keystore clean up our API Gateway team still seeing these kind of errors. Not sure why it's happening. can you please advise?
I am also including our API Gateway dashboard screenshot for reference. Red indicates failure attempts and Green indicates success.
Thank you,
Naveen
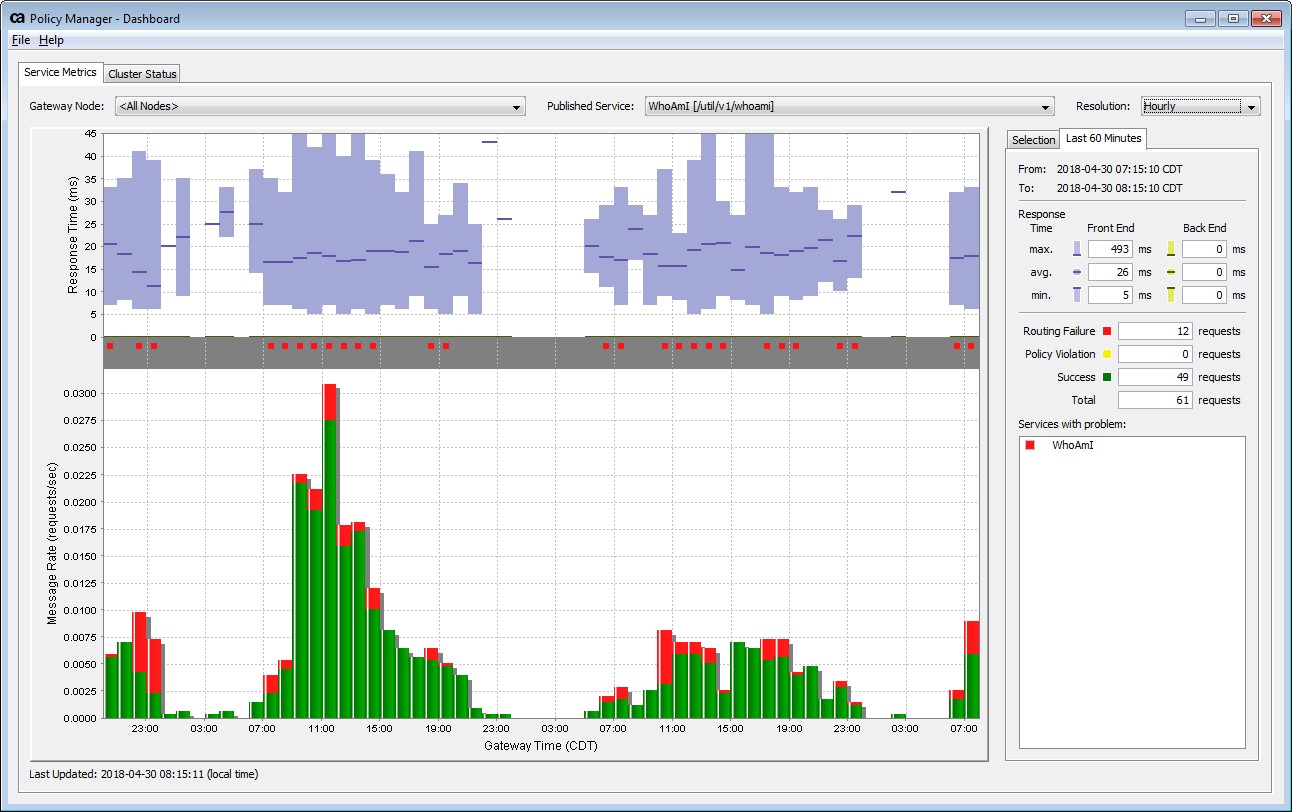
But I am able to decode the SMSESSION by using webagent SDK.
Attribute name : DEVICENAME
Attribute value: ServerName
Attribute name : USERDN
Attribute value: CN=XXXXX,OU=***,OU=***,DC=XXXX,DC=XXXX,DC=***
Attribute name : SESSIONSPEC
Attribute value: Ly4LVWM1C6brHrbAAauzly1W3nkAf2khgsoFen6+dz9TfkD4he+6yfZDEurkdJBiJSGF61LodOAPwbXkCQpVUbNIwThx3QntMlHtLi6KBkJfizs0Xprg4Qbq+r+ZedSlHmEpPxrv6i60477Nc8D7GWH3bpYNRQFTu137KIngRfKH0YZH9va32DP/0AWtgQ3wuZxM0B7eIaL8AbNvJM7f4VbWjDnw/2AhHeJs9genJiPYd986sezgF/RsqdLlFOlfpSSLNVLALrNvBekMoboxaqhv2AYuhEbTyUycL1TU3dfRWZVKCF1wbDP3trqoqlJtEOyDhjijZBseZXBoQDlZUrCAOhQk2ohoS1CK6d5tgJGygtk+qCLQAaFDLrqCbZWoYXSU/x4VZLKQDwDr27L3aZPDBtNh73UNLsndupujYLlPkSM4d23kTzqL8YjTnk1ZQBgbqJ0+S0MdGcOuCLIE4bJOxJc0FEjP74MEtK+MtJvVw2w2b6AW0efLjKhZYXIK
Attribute name : SESSIONID
Attribute value: 9P+B+6p3nPDoHYuFJZYQ3X5jdGk=
Attribute name : USERNAME
Attribute value: CORPORATE\***
Attribute name : CLIENTIP
Attribute value: 10.86.191.30
Attribute name : IDLESESSIONTIMEOUT
Attribute value: 0
Attribute name : MAXSESSIONTIMEOUT
Attribute value: 622393886
Attribute name : STARTSESSIONTIME
Attribute value: 1525089754
Attribute name : LASTSESSIONTIME
Attribute value: 1525092508
Attribute name : UNKNOWN
Attribute value: SM
UserID: CN=***,OU=XXXX,OU=XXXX,DC=XXXX,DC=XXXX,DC=***
Session start time: 04/30/2018 07:02:34
Last session time : 04/30/2018 07:48:28
Don't worry the XXXX's. Because it's a real user i masked those values. One Odd thing i noticed is the Max Session timeout value. It's very high.