Hello Everyone,
Currently we are facing an issue with a federation if it is sp-initiated. Here is the overview:
Service provider is sending the following Authentication request by using HTTP-POST binding:
[05/18/2018][16:10:37.165][16:10:37][2715][3939908464][AuthnRequestProtocol.java][setAuthnRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][<samlp:AuthnRequest
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
ID="ONELOGIN_540abdf191c46801f9552dd177eb3d16fba3150c"
Version="2.0"
IssueInstant="2018-05-18T21:10:36Z"
Destination="https://idp.com/affwebservices/public/saml2sso"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
AssertionConsumerServiceURL="https://saml-ppr.sightcall.com/v2/acs/5pub0vowbepf">
<saml:Issuer>https://sp.com/v2/5pub0vowbepf</saml:Issuer>
<samlp:NameIDPolicy
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"
AllowCreate="true" />
<samlp:RequestedAuthnContext Comparison="exact">
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
</samlp:AuthnRequest>]
Our Federation Configuration:

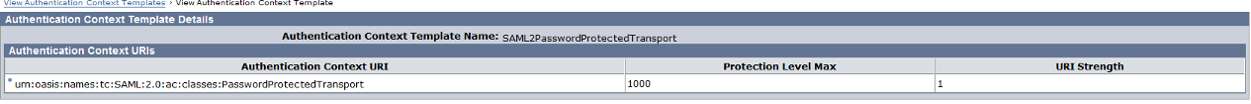
Even I am using AuthnContext Template as "urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport" in IDP side to match the Authentication request of SP my federation is still failing when i try sp-initiated URL. Here are the smtracedefault logs:
smtracedefault log:
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][verifySignatureOnRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Request does not contain a signature to verify.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:710][GetDsUserProp][][][][][][][][][][][][][][][][][][][][][Enter function GetDsUserProp]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:2182][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][][][][][][][][][Enter function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:2213][GetPropIndex][][][][][][][][][][][][][][][][][][][][][Processing Attribute [Property = SM_AUTHENTICATIONLEVEL] [Trim Property = SM_AUTHENTICATIONLEVEL] [Separator = ^]]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:2514][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][true][][][][][][][][Leave function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:738][GetDsUserProp][][][][][][][][][][][][][1][][][][][][][][Leave function GetDsUserProp]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AuthnRequest is retrieved:
com.netegrity.SAML2Gen.impl.AuthnRequestImpl@c36b81]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateDestination][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Enter validateDestination]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateDestination][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Using Proxy URL: https://idp.com/affwebservices/public/saml2sso]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateDestination][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Destination matches local URL.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateDestination][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Exit validateDestination]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][The binding contained in the AuthnRequest is: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Validating AuthnRequest Version ...]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AuthnRequest version is 2.0]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Configured supporting version is 2.0]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AuthnRequest Version is valid.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Validating AuthnRequest Issuer ...]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequestIssuer][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Issuer format is "urn:oasis:names:tc:SAML:2.0:nameid-format:entity"]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AuthnRequest Issuer is valid.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Validating AuthnRequest NameIDPolicy ...]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateNameIdPolicy][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Requesting NameIDPolicy format is urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AuthnRequest NameIDPolicy is valid.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Configured NameID format is "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Verified nameid policy exists [CHECKPOINT = SSOSAML2_IDPNAMEIDPOLICY_VERIFY]]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Identity Provider is not allowed to create a new identifier to represent the principal.]
[05/18/2018][16:10:37.174][16:10:37][2715][3939908464][SmAuthUser.cpp:710][GetDsUserProp][][][][][][][][][][][][][][][][][][][][][Enter function GetDsUserProp]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmAuthUser.cpp:2182][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][][][][][][][][][Enter function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmAuthUser.cpp:2213][GetPropIndex][][][][][][][][][][][][][][][][][][][][][Processing Attribute [Property = afiExternalUserID] [Trim Property = afiExternalUserID] [Separator = ^]]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:1190][][][][][][][][][][][][][][][][][][][][][][LogMessage:ERROR:[sm-Ldap-02230] Error# '81' during search: 'error: Can't contact LDAP server' Search Query = 'afiExternalUserID=*']
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:501][CSmDsLdapConnMgr::AddDeadHandleList][][][][][][][][][][][][][][][][][][][][][Marked dir connection (seq: 1117) 10.68.9.10:636 as Close Pending]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:501][CSmDsLdapConnMgr::AddDeadHandleList][][][][][][][][][][][][][][][][][][][][][Marked dir connection (seq: 1121) 10.68.9.10:636 as Close Pending]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:501][CSmDsLdapConnMgr::AddDeadHandleList][][][][][][][][][][][][][][][][][][][][][Marked user connection (seq: 1118) 10.68.9.10:636 as Close Pending]
[05/18/2018][16:10:37.175][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:501][CSmDsLdapConnMgr::AddDeadHandleList][][][][][][][][][][][][][][][][][][][][][Marked user connection (seq: 1122) 10.68.9.10:636 as Close Pending]
[05/18/2018][16:10:37.178][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:895][IsAvailable][][][][][][][][][][][][][][][10.68.9.10][636][][][][][Successful V3 Bind server]
[05/18/2018][16:10:37.179][16:10:37][2715][3939908464][SmDsLdapConnMgr.cpp:628][PingServer][][][][][][][][][][][][][][][10.68.9.10][636][][][][][LDAP Server Ping Successful]
[05/18/2018][16:10:37.187][16:10:37][2715][3939908464][SmAuthUser.cpp:2514][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][true][][][][][][][][Leave function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.187][16:10:37][2715][3939908464][SmAuthUser.cpp:738][GetDsUserProp][][][][][][][][][][][][][10][][][][][][][][Leave function GetDsUserProp]
[05/18/2018][16:10:37.187][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Configured NameID: value of the User Attribute "afiExternalUserID"]
[05/18/2018][16:10:37.187][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Validating the retrieved NameID (length: 10 value: 0001061200]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][retrieveNameID][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][The retrieved NameID value is valid.]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][User Name Identifier from IdP resolved.]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][IgnoreReqAuthnContext = false]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateRequest][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Validating AuthnRequest RequestedAuthContext ...]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateAuthnContext][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Verifying the requested authnContext uri]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateAuthnContext][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Comparsion type is exact]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][identifySessionAuthnContext][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Getting authnContext list]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][SmAuthUser.cpp:710][GetDsUserProp][][][][][][][][][][][][][][][][][][][][][Enter function GetDsUserProp]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][SmAuthUser.cpp:2182][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][][][][][][][][][Enter function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][SmAuthUser.cpp:2213][GetPropIndex][][][][][][][][][][][][][][][][][][][][][Processing Attribute [Property = SM_AUTHENTICATIONLEVEL] [Trim Property = SM_AUTHENTICATIONLEVEL] [Separator = ^]]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][SmAuthUser.cpp:2514][CSmAuthUser::GetPropIndex][][][][][][][][][][][][][true][][][][][][][][Leave function CSmAuthUser::GetPropIndex]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][SmAuthUser.cpp:738][GetDsUserProp][][][][][][][][][][][][][1][][][][][][][][Leave function GetDsUserProp]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][identifySessionAuthnContext][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][Session authentication level: 5]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AuthnRequestProtocol.java][validateAuthnContext][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][RequestedAuthnContext uri urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport undefined in the template]
[05/18/2018][16:10:37.188][16:10:37][2715][3939908464][AssertionGenerator.java][invoke][c3fbb450-39f84296-a4d7c5ee-0aa234ac-29739e6f-4][][][][][][][][][][][][][][][][][][][][AssertionHandler preProcess() encountered few errors, it returns:<Response ID="_79a7bee7331f4fdcc374d9791bea8817ba8f" InResponseTo="ONELOGIN_540abdf191c46801f9552dd177eb3d16fba3150c" IssueInstant="2018-05-18T21:10:37Z" Version="2.0" xmlns="urn:oasis:names:tc:SAML:2.0:protocol">
<ns1:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity" xmlns:ns1="urn:oasis:names:tc:SAML:2.0:assertion">AMFAMSAMLNEW</ns1:Issuer>
<Status>
<StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Requester">
<StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:NoAuthnContext"/>
</StatusCode>
<StatusMessage>The RequestedAuthnContexts in AuthnRequest are not supported.</StatusMessage>
</Status>
</Response>
]
Any help is greatly appreciated.
Thank you,
Naveen
Environment details:
SSO Policy server version : 12.52 SP1 CR06
SSO AdminUI version : 12.52.0106.2209
SiteMinder web agent version : 12.52 SP1 CR05
SiteMInder webagent option pack version : 12.52 SP1 CR05
Application Server serving affwebservices: Jboss 6