Hi
I have follow these steps
With simple curl request passing the client certificate and calling the api with client authentication assertion, it works (tls gone fine and the api response is 200).
If i try with firefox browser or internet explorer i receive the following message:
---
Secure Connection Failed
An error occurred during a connection to fqdn:7443. SSL peer cannot verify your certificate. (Error code: ssl_error_bad_cert_alert)
The page you are trying to view cannot be shown because the authenticity of the received data could not be verified.
Please contact the web site owners to inform them of this problem.
--
I have import the pfx of client certificate inside the firefox personal certificate store, the root CA cert inside Server Section and also in Windows Trust Certification Store
Also in trust store of layer 7 there is the cer client certificate.
What could missing inside Layer 7 api service configuration ?
Thanks in advance
Original Message:
Sent: 08-11-2015 11:30 AM
From: Nathan Blumenthal
Subject: Re: Configuring mutual ssl
- You first need to import a public key, i.e. certificate of your backend destination into the gateway's trust store. You then need to export your gateway's certificate into your backend destination trust store.
- To import cert:
- Go to Tasks > Manage Certificates
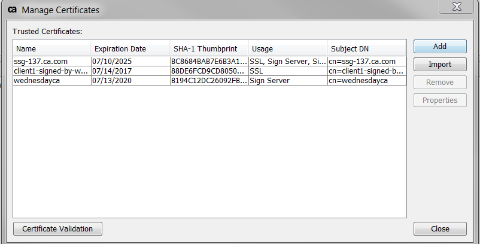
- Click Add on the right
- Add via file, or via http connection
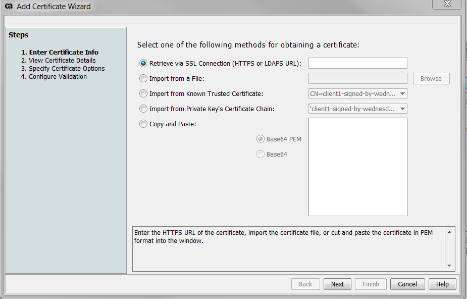
- To export cert:
- Go to Tasks > Manage Private Keys
- Click on the Private Key called "ssl" and click Properties on the right
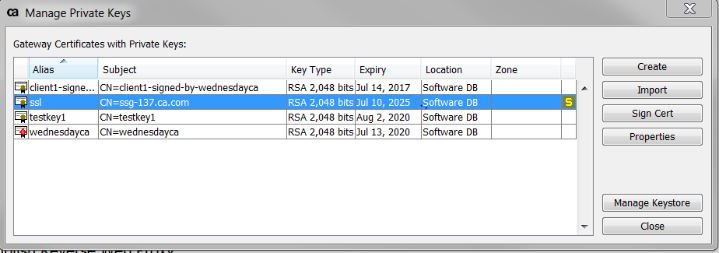
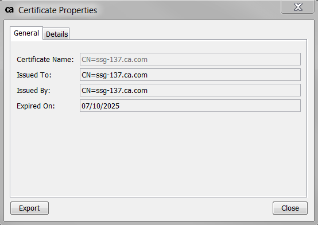
- Then click View Certificate
- Then Click Export
2. You then need to create a user either in your Internal Identity Provider or another IDP, in which the username is the same name of the certificate cn. Then attach the imported certificate to that user.
- Click the Identity Providers tab in the top left
- Right click on the Internal Identity Provider and click Create User
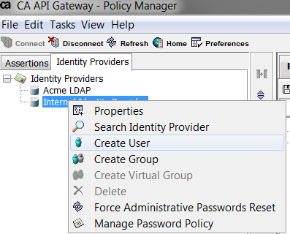
- Make sure to make the user name the same name as your destination cn on your imported certificate from the backend.
- Make sure to check Define Additional Properties
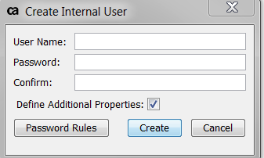
- Click Create
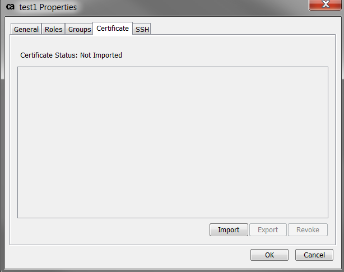
- On the next screen go the Certificate tab, and import the same certificate you did from the first steps. Confirm the cn of this cert matches this user's name.
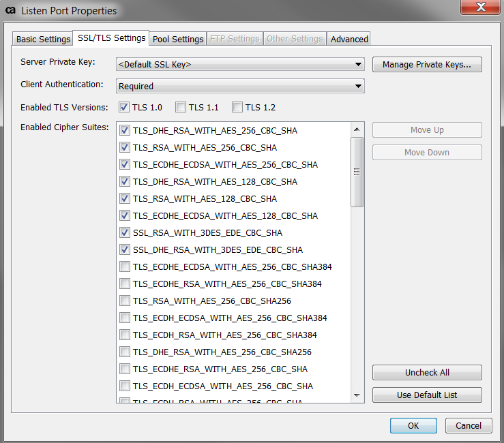
3. You then need to make a listen port require client authentication. In my case I usually make 9443 require client auth.
- Go to Tasks > Manage Listen Ports
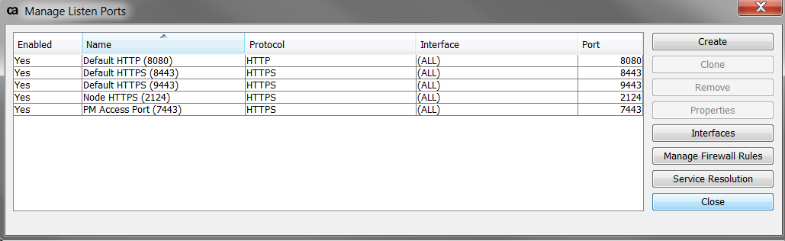
- Click on the Default HTTPS (9443) and click Properties on the right
- Go the the SSL/TLS Setting tab and make sure Client Authentication dropdown says Required.
4. In policy, drag the "Require SSL or TLS Transport with Client Authentication" assertion. Make sure when calling this policy/endpoint you are using the port that requires client auth. Below it, drag in an "Authenticate against Internal Identity Provider" assertion, or could use Auth against User or Group and specify the certificate user.
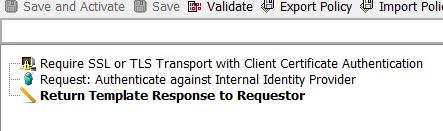

- Note: If going from browser to only hit a service on the gateway, then you need to import your key pair into your browser. If going to from one gateway to another, your backend gateway needs to have the Require SSL or TLS with Client Certificate Authentication. If hitting a backend service, you need to configure that backend to enforce mutual SSL using the imported certificate.