abriones
The authorization failure is not necessarily due to User Policy. In federation it could be due to variety of reasons beyond User Policy. The only way to confirm what happened is to look at the Policy Server Trace logs.
Please enable Policy Server Trace Logging. This would tell you why the Policy Server returned to WAOP an authorize failure. Make sure we have selected 'Fed Server' in component. I've also provided a snippet of the smtracedefault.txt file which you could copy directly into your smtracedefault.txt before enabling trace logging.
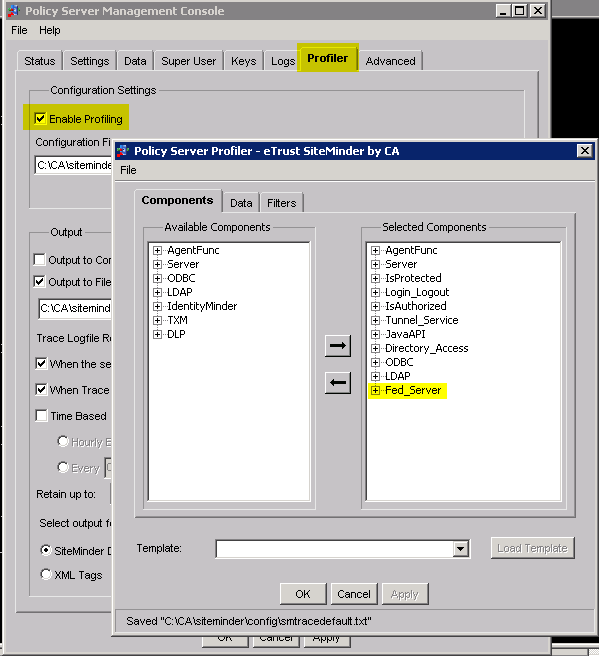
Snippet of C:\CA\siteminder\config\smtracedefault.txt
components: AgentFunc/Init, AgentFunc/UnInit, AgentFunc/IsProtected, AgentFunc/Login, AgentFunc/ChangePassword, AgentFunc/Validate, AgentFunc/Logout, AgentFunc/Authorize, Server/Policy_Server_General, IsProtected, Login_Logout, IsAuthorized, Tunnel_Service, JavaAPI, Directory_Access, ODBC/Sql_Statement_Begin_End, ODBC/Sql_Errors, ODBC/Connection_Monitor, LDAP/Ldap_Call_Begin_End, LDAP/Internal_Operation, LDAP/Ldap_Error_Messages, Fed_Server
data: Date, PreciseTime, SrcFile, Function, TransactionName, Message, Data, AgentName, Resource, User, Group, Realm, Domain, Directory, Policy, Rule, ActiveExpr, Expression, ErrorValue, ReturnValue, ErrorString, IPAddr, IPPort, Result, Returns, CallDetail, AuthScheme, AuthReason, AuthStatus, Query
version: 1.1
Regards
Hubert