Hi Veera,
Your understanding is correct.
The "sessionToken" returned from Auth/AZ web service call is nothing but SMSESSION cookie.
So, if you are going to do SSO with another SPS Auth/AZ java agent, you will basically need to send this token instead of username and password.
Similarly, if you are going to do SSO with another normal web agent, you will need to create an SMSESSION cookie with this sessionToken value and send this along with your request.
Here is how I tested this to verify :
1. First using SPS Auth/AZ web service and using username and password create the sessionToken

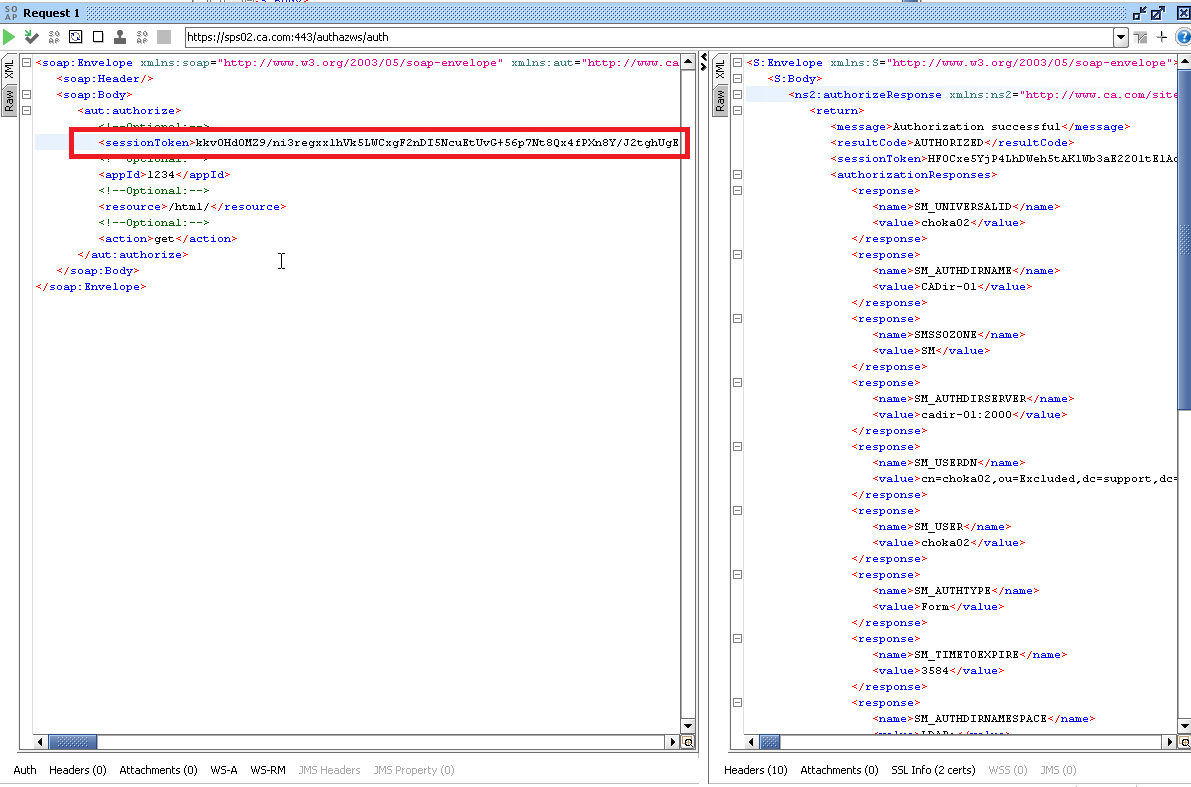
2. Next, for any consequent request, you can send this token and perform SSO instead of sending username and password again :
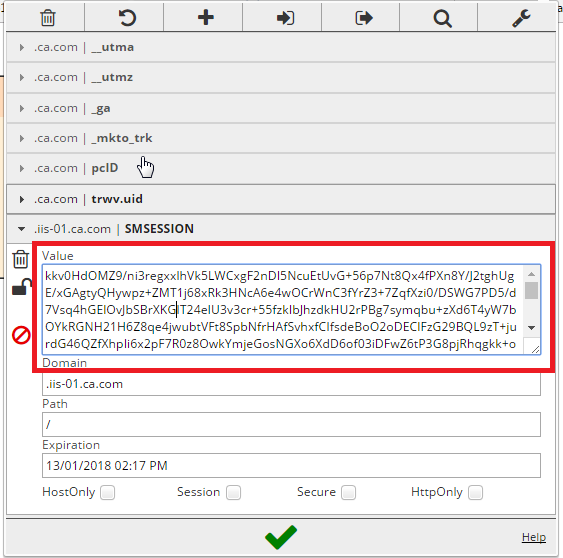
3. Next, to test the SSO with the normal web agent, in chrome browser using "EditThisCookie" plugin I manually created SMSESSION cookie using the sessionToken value returned from SPS Auth/AZ authentication call :
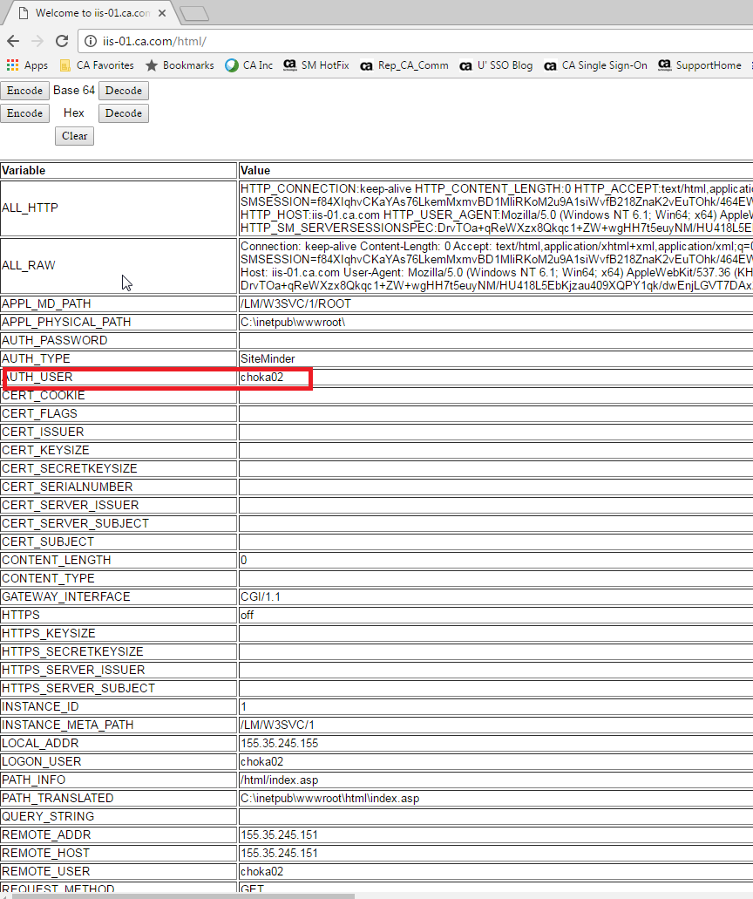
4. Then, in the same browser session , I was able to access the protected resource without any challenge. This confirms I was able to perform SSO to the normal web agent protected resource using the sessionToken generated by SPS Auth/AZ web service :
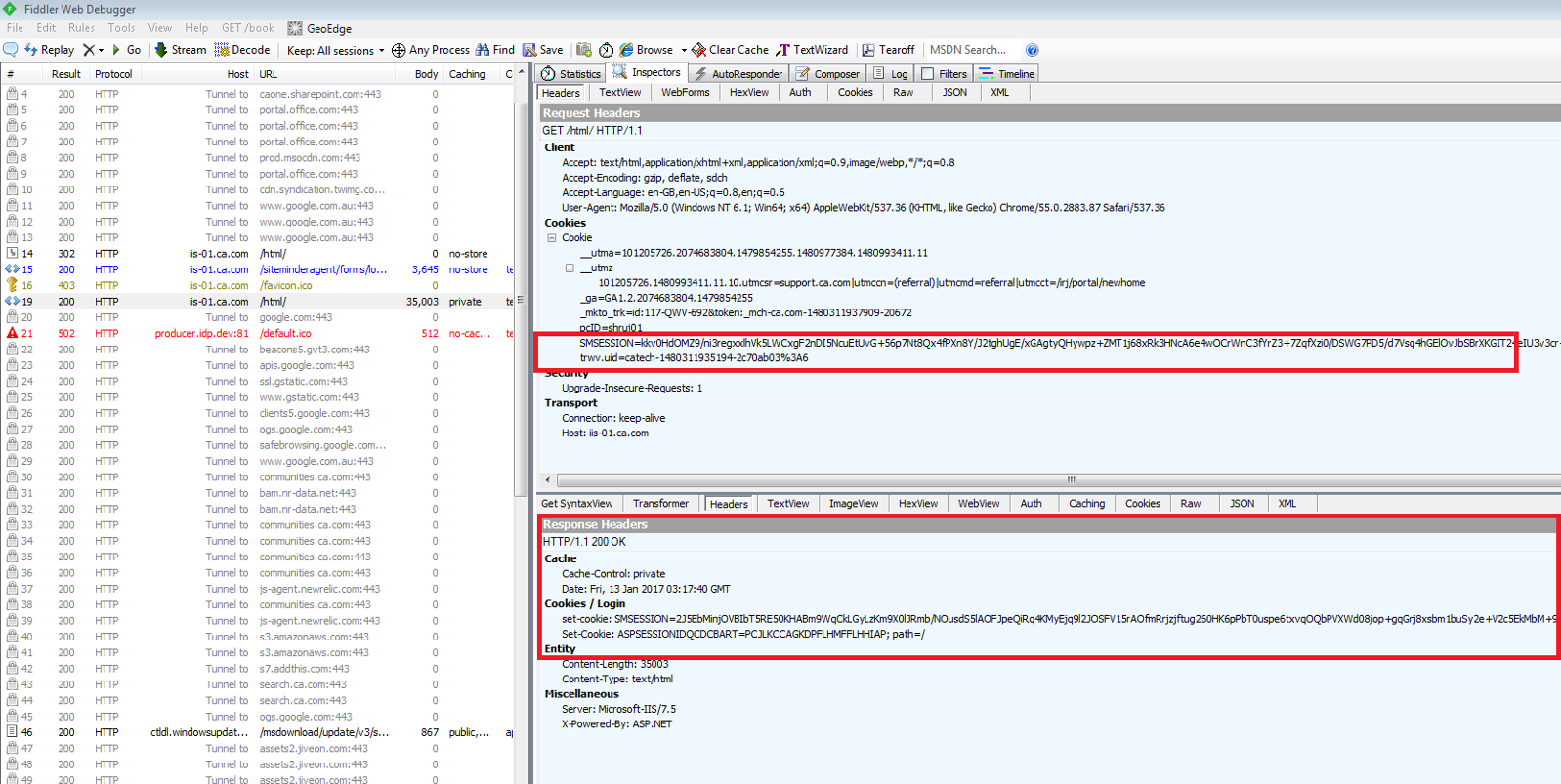
Hope this clarifies your question.
Cheers,
Ujwol Shrestha
Ujwol's Single Sign-On Blog