Makesh summarized Part-A of the question which focus on FO / LB.
I'll take elaborate on Part-B.
| Part-B |
|---|
We theorized that since it doesn't hold a database of its own and makes a connection to the policy server it must leech the data from the policy store and thus could be redundant without the need for manual duplication. Would this be correct? |
It is unclear as to what data are we taking about with specific i.e. Access Policy Data OR CA AG Configuration Data. You do hint Policy Store, but alas Policy Store can also hold more than just Access Policy in this case. So I'm going to talk about both so as to give you an extended preview.
Access Policy Data : This is stored in Policy Store. Hence it is retrieved as you described.
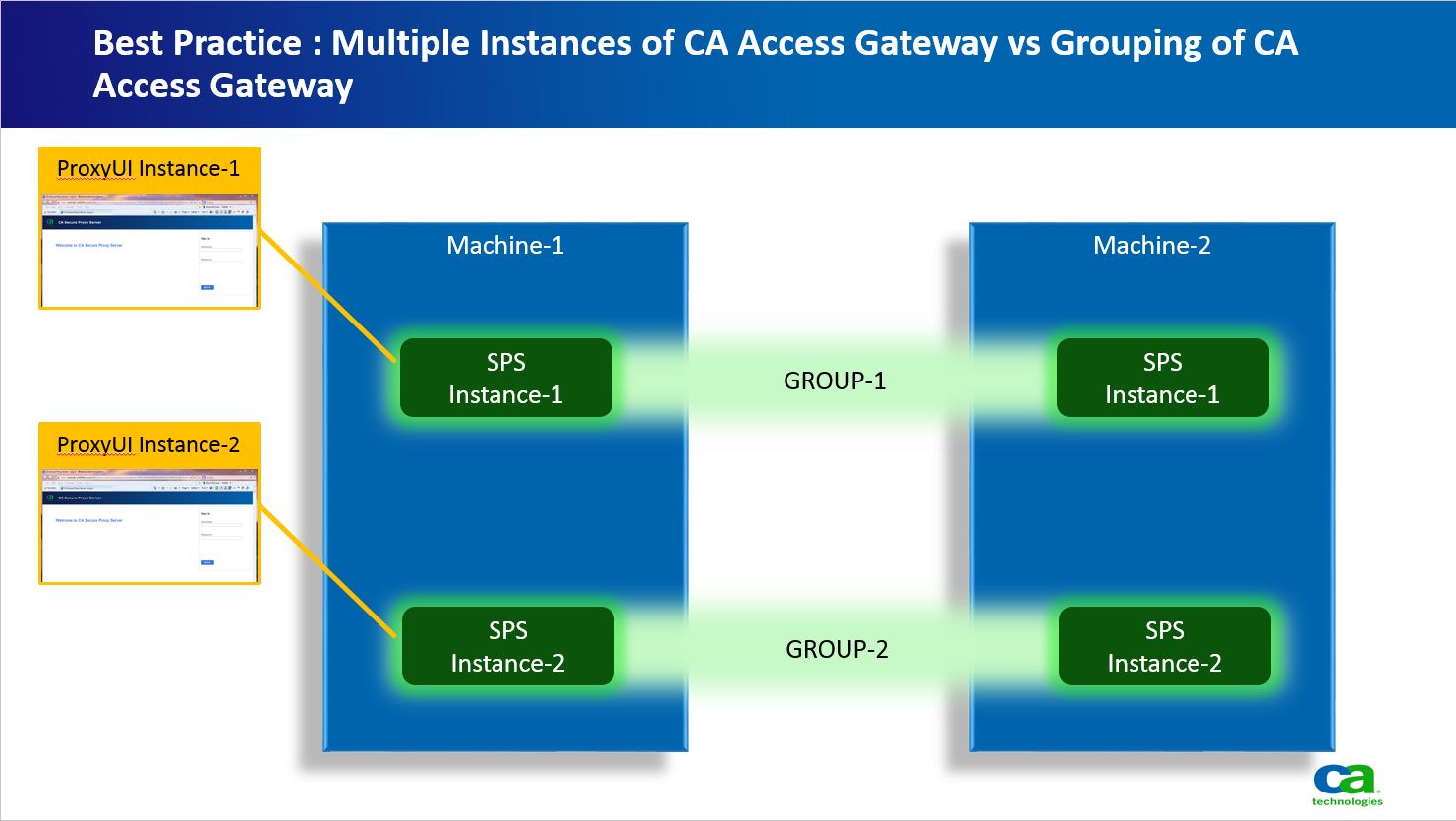
CA AG Configuration Data : OOB resides on the filesystem that CA AG is configured. Thus OOB configuration being filesystem based plus being nuclear to each CA AG instance, are manually synced by hand on individual CA AG OR use individual proxuyi to manage / administer individual instance. If we want to administer / manager a Cluster of CA AG using a Single ProxyUI, then we switch the solution to a Group Based Solution. Here we can group "n" number of CA AG into Clusters. Once Clustered all configuration data is saved into Policy Store instead of filesystem. NOTE : This Cluster is only for configuration purposes. Once clustered all CA AG in the cluster retrieve their configuration from Policy Store. Thus we can use a single ProxyUI to manage / administer multiple CA AG. But be careful of what CA AG instances you cluster e.g. you cannot cluster two CA AG running on two different ports. Again their are Pros and Cons in each approach (e.g. if you are having a DevOPS methodology then sync using scripting individual CA AG sounds appropriate rather than UI).