Good afternoon,
To add to what Sascha added on how to implement this. You will need to do the following:
1) Copy the OTK grant type=Password policy located under the OTK/Policy Fragments/grant_types folder to the OTK/Customizations/grant_types folder with a name like OTK grant type=Password Custom
2) Clone the OTK grant_type=Password encapsulated assertion to the new name OTK grant type=Password Custom
3) Update the auth/oauth/v2/token policy so that the OTK grant type=Password is comment out and you add in the new encapsulated assertion OTK grant type=Password Custom
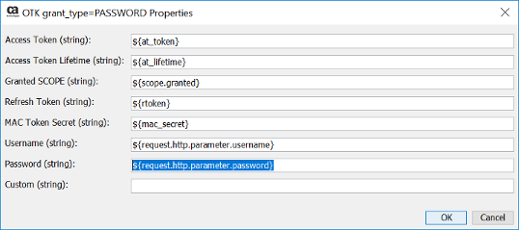
4) Update the OTK User Attribute Look Up Extension policy to send back all the information that you need as it will be pulled back through the OTK User Authentication assertion
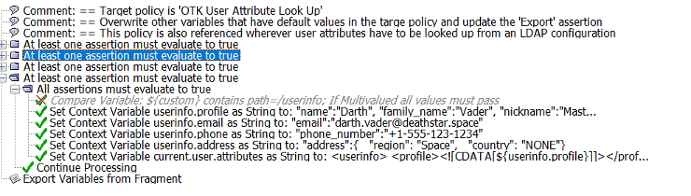
as the variable ${current.user.attributes} in XML format
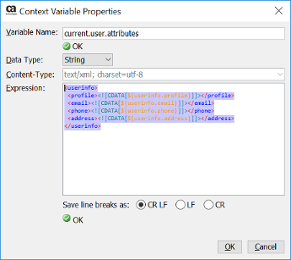
5) Modify the OTK grant type=Password Custom policy to return back the token by modifying the context variable clientResponse with values pulled from the XML
Sample Policy attached
Sincerely,
Stephen Hughes
Broadcom Support