Hi gurus,
last day I have a issue with a my monitoring solution. First all I didn't setup any rule on the Agent, it is only do nothing..
I checked with top which app is consuming CPU ..
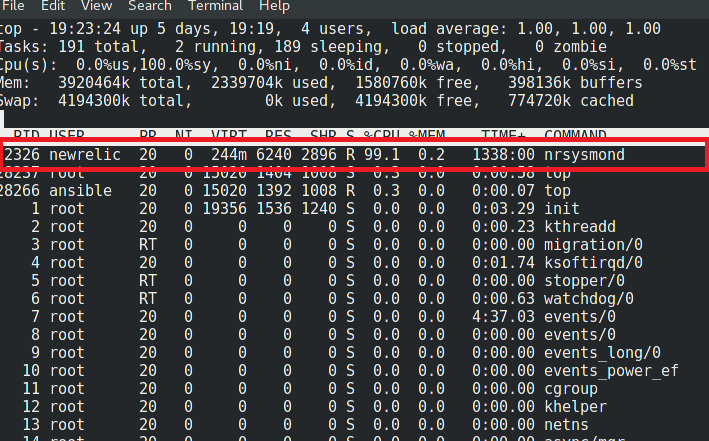
So I checked with secons kernel syscalls
[root@it-lin-fxs-web-01 bin]# ./secons -sc
CA ControlMinder secons v12.81.0.2878 - Console utility
Copyright (c) 2013 CA. All rights reserved.
Active system calls:
syscall #2 - PID: 2326
syscall #43 - PID: 9837 9835 9834 9831 4037 2418 592 9836 2415 9830 593 591 9833 9832 2409 2414 3793 3798 2198 3798
I checked with ps tool which program has PID 2326
[root@it-lin-fxs-web-01 bin]# ps --ps -fea | grep 2326
newrelic 2326 2324 12 Jul12 ? 17:25:02 /usr/sbin/nrsysmond -c /etc/newrelic/nrsysmond.cfg -p /var/run/newrelic/nrsysmond.pid
So, Is CA PIM Blocking any monitoring tool kernel syscall?
Regards