Hello Gustavo,
There are a couple of things that you need to take into consideration:
1) that you will need to have an organisation created for the user that logs in, otherwise it will not allow you to log in.
2) if you use SAML, you need to put the user details in the attributes elements.
here are the settings that I was able to use in my portal (4.2.x)
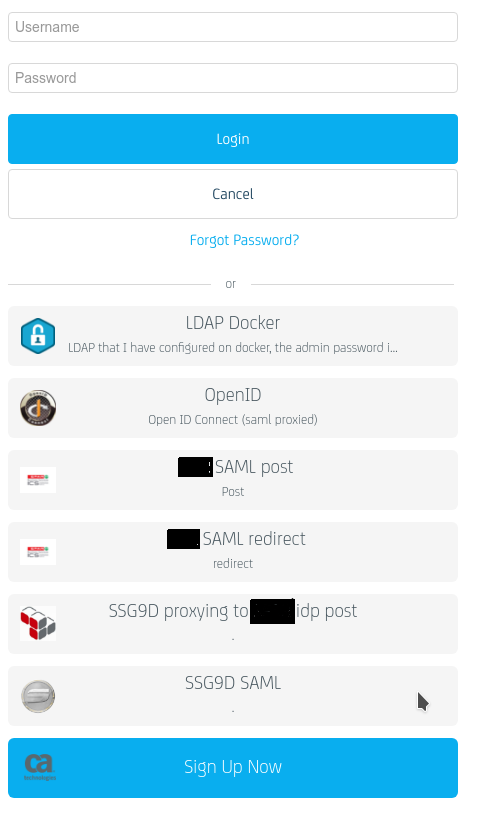
Where in some, I use the Gateway as an idp to SAML 'proxy',
here is an example of the setting for LDAP
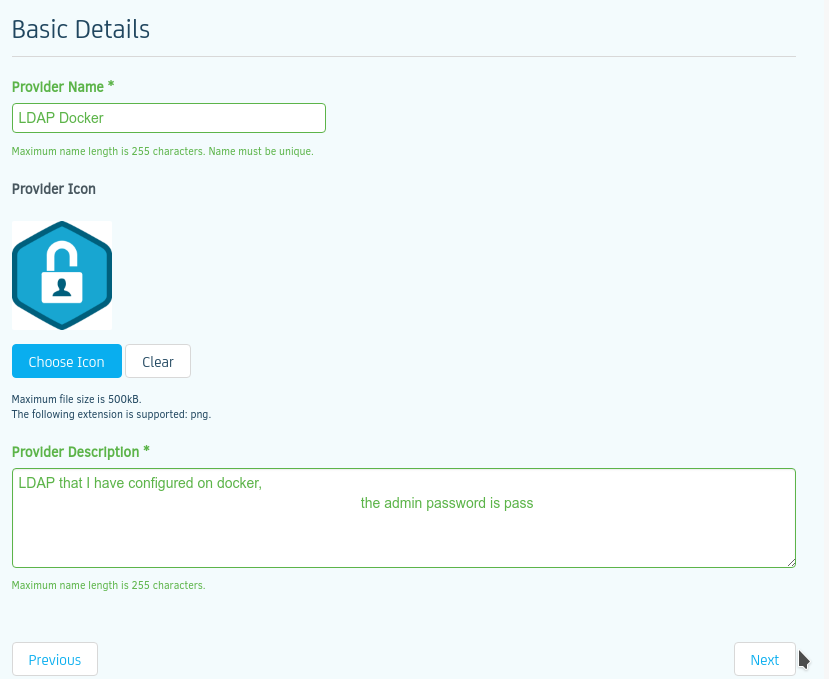
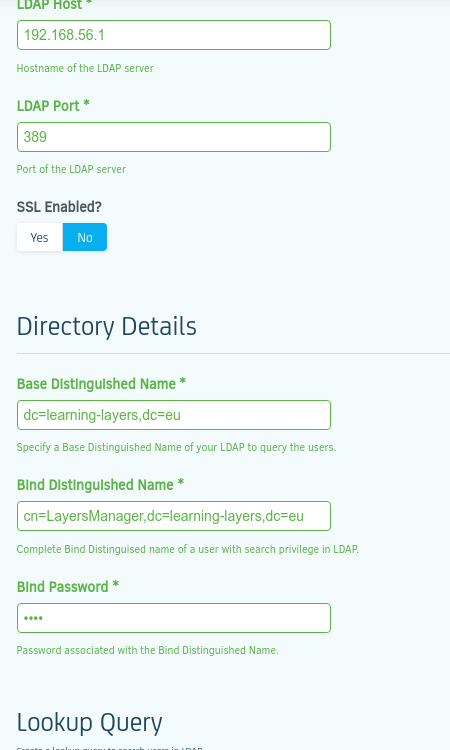
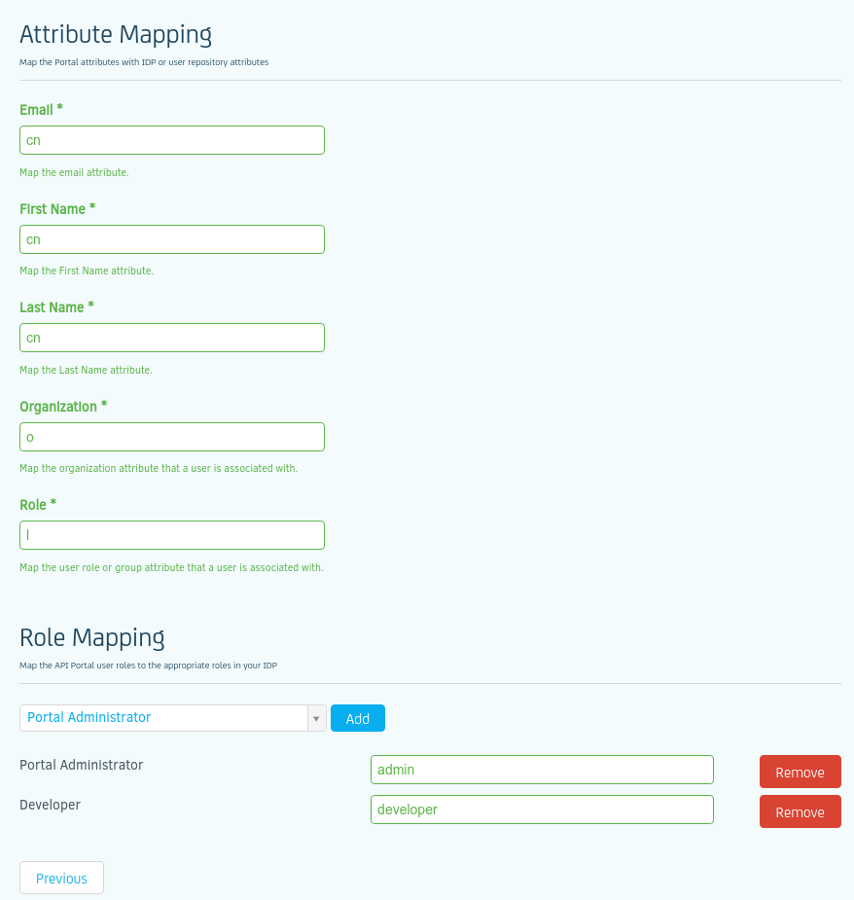
As you can see, I am reusing LDAP fields so that all will go through and in the Organisation I have 'o' ,
in ORGANISATIONS I have
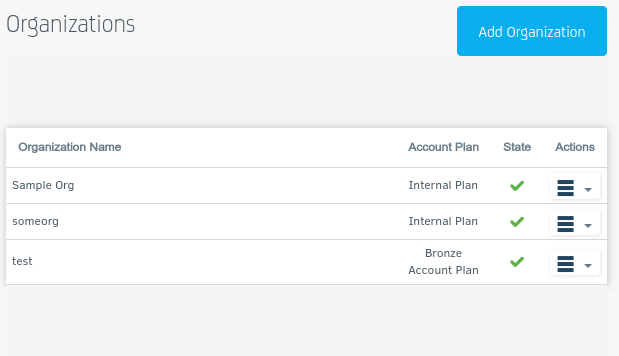
and in the LDAP I have the following user:
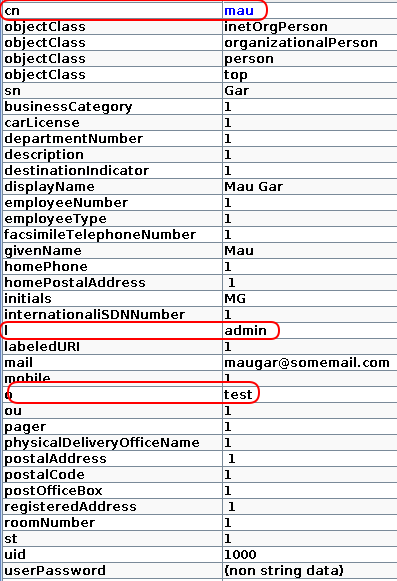
As you can see I use 'o' for the organisation but I HAD to create it manually in the portal under the 'Organisation' page,
I hope this helps
For SAML, here is a sample SAML response that works
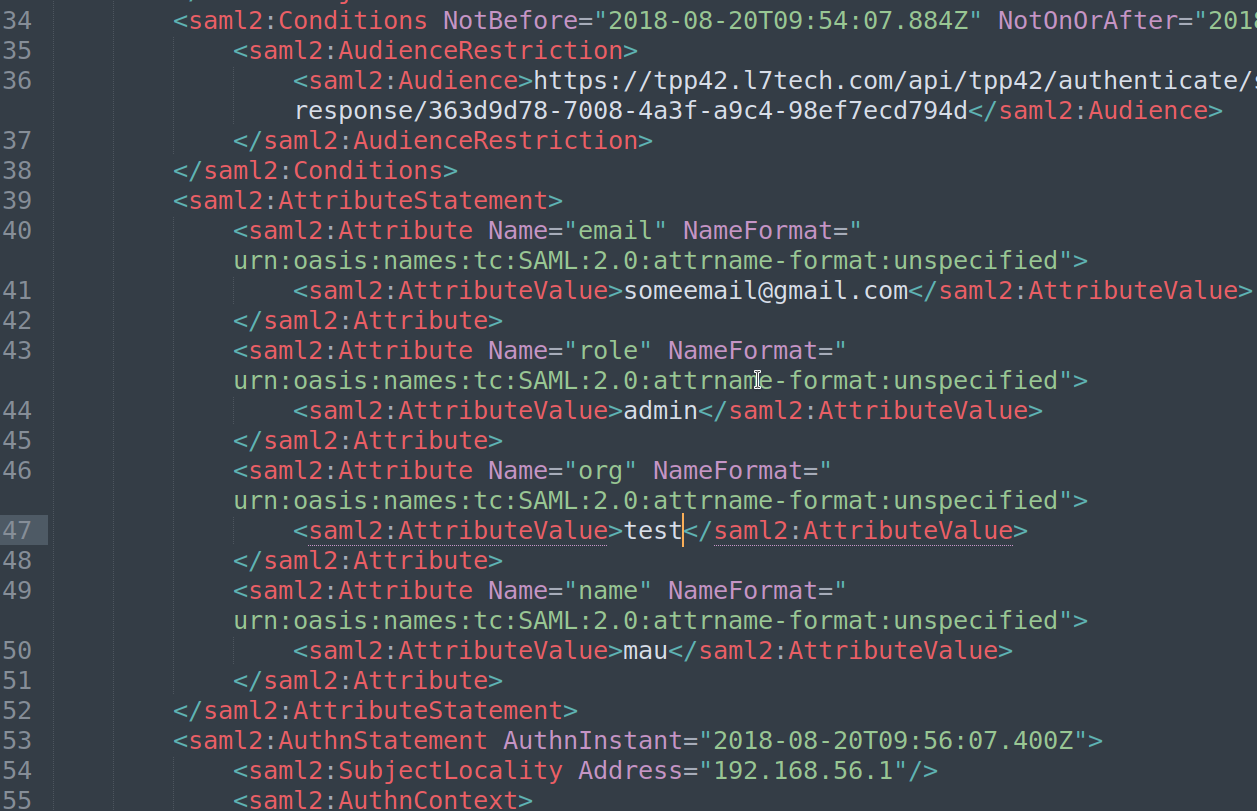
I hope this helps