Team,
The preferred CLI (command-line-interface) process to sync Identity Manager Global Users to provisioning roles was IMPS\bin\etautil binary.
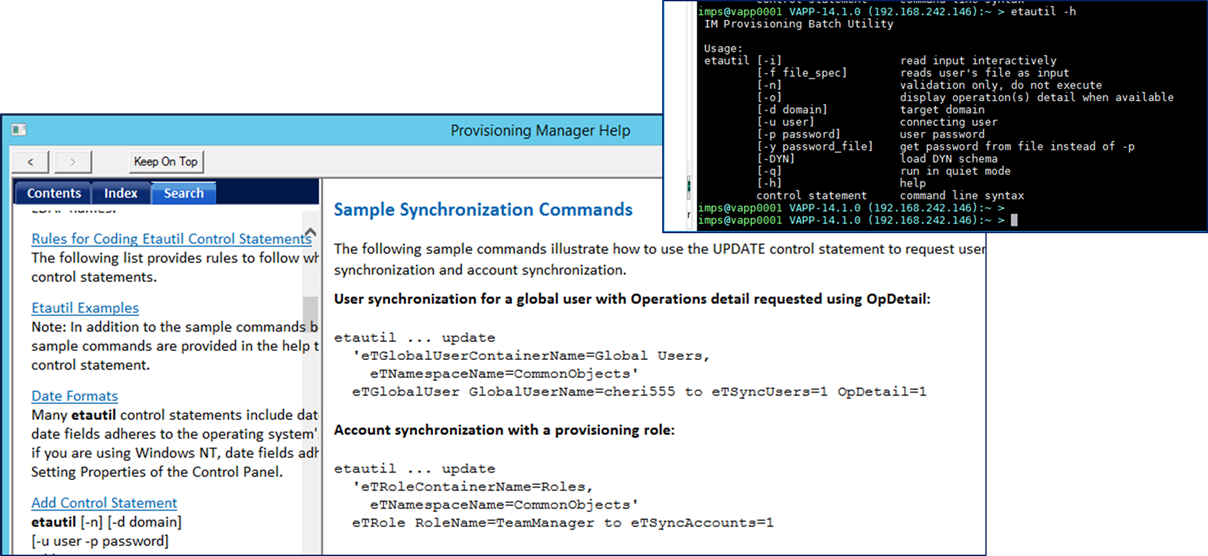
However, I wish to show how to leverage any LDAP modify client tool, e.g. CLI or GUI, to emulate the same behavior.
- FYI: The IMPS bin folder, the IMPS GUI bin folder, and the CCS bin folder, all contain a ldapmodify binary; or you may wish to use CA Directory dxmodify binary.
Using the CA Directory transparent routers, we can capture the sync operation from the IME via the JIAM ldap call to the IMPS Service over TCP 20389/20390. This sync operation requires the IMPS service to function, and would not work with a direct call/update to the provisioning directory, which is never advised to avoid impacting referential integrity of the data tier. Ex: Transparent Router(s) for Identity Management Provisioning Tier - DXLINK
Step 1: Using a transparent router, with trace mode equal to dsa or ldap, we can capture the following during a IME sync user to roles.
#admin_router_imps_20499_trace.log-> [2] invoke-id = 2 credit = 999999
#admin_router_imps_20499_trace.log-> [2] Entry:
#admin_router_imps_20499_trace.log-> [2] <cosineDomainComponent "eta">
#admin_router_imps_20499_trace.log-> [2] <cosineDomainComponent "im">
#admin_router_imps_20499_trace.log-> [2] <eTNamespaceName "CommonObjects">
#admin_router_imps_20499_trace.log-> [2] <eTGlobalUserContainerName "Global Users">
#admin_router_imps_20499_trace.log-> [2] <eTGlobalUserName "4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d">
#admin_router_imps_20499_trace.log:> [2] Remove-attr: eTSyncUsers
#admin_router_imps_20499_trace.log:> [2] Add-attr: (eTSyncUsers "1")
#admin_router_imps_20499_trace.log-> [2] Remove-attr: eTUseOperationID
#admin_router_imps_20499_trace.log-> [2] Add-attr: (eTUseOperationID "b28a17b8-679c-493f-94ef-829350f02a49")
#admin_router_imps_20499_trace.log-> [2] Remove-attr: eTUpdateNode
#admin_router_imps_20499_trace.log-> [2] Add-attr: (eTUpdateNode "DC2012")
#admin_router_imps_20499_trace.log-> [2] flags = IDU_FLAGS_USE_SSL
Step 2: Convert the above format into an ldapmodify input file, e.g. *.ldt
- Note1: I had to convert this operation into two (2) operations to avoid an error message for eTSyncUser attribute:
XXXXX modification failed: Attribute 'eTSyncUsers' cannot be modified in same request with incompatible changes
- Note2: The eTUseOperationID must be an unique string, e.g. GUID
I tested with a random text string to find out any limitation.
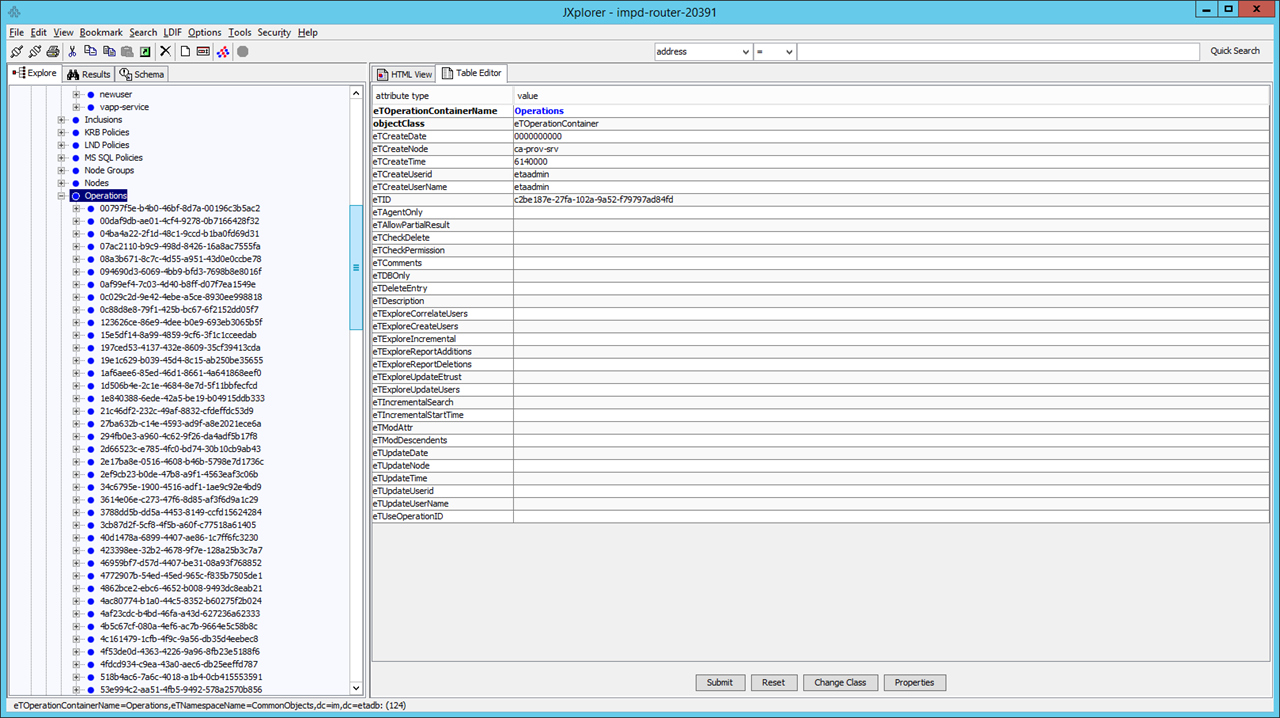
This value will be placed in the IMPD branch to be compared for uniqueness.
eTOperationID=XXXXX,eTOperationContainerName=Operations,eTNamespaceName=CommonObjects,dc=im,dc=etadb
- Note3: Ignore the standard ldapmod operations error/warning message; as it has no impact to the sync operation.
dn: eTGlobalUserName=4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d,eTGlobalUserContainerName=Global Users,eTNamespaceName=CommonObjects,dc=im,dc=eta
changetype: modify
delete: eTSyncUsers
-
delete: eTUseOperationID
-
delete: eTUpdateNode
-
dn: eTGlobalUserName=4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d,eTGlobalUserContainerName=Global Users,eTNamespaceName=CommonObjects,dc=im,dc=eta
changetype: modify
add: eTUseOperationID
eTUseOperationID: Insert-A-Random-GUID-Here-Alan-Was-Here2
-
add: eTUpdateNode
eTUpdateNode: using-ldapmodify-update-example-not-a-node-name-here
-
add: eTSyncUsers
eTSyncUsers: 1
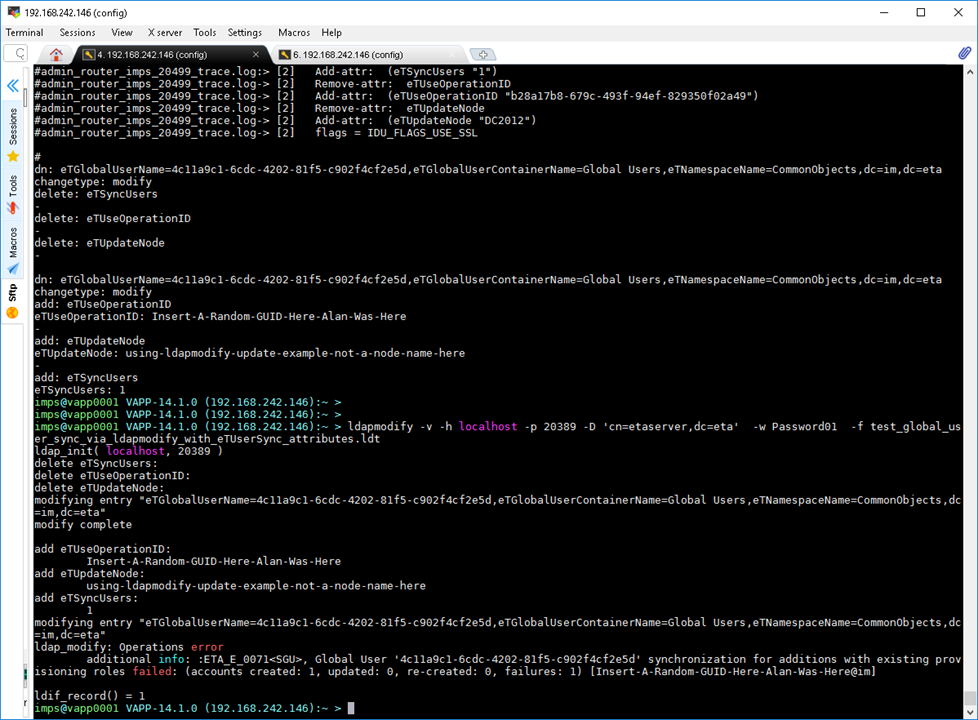
Step3: Execute the newly created input file with your favorite ldap client tool (cli or gui).
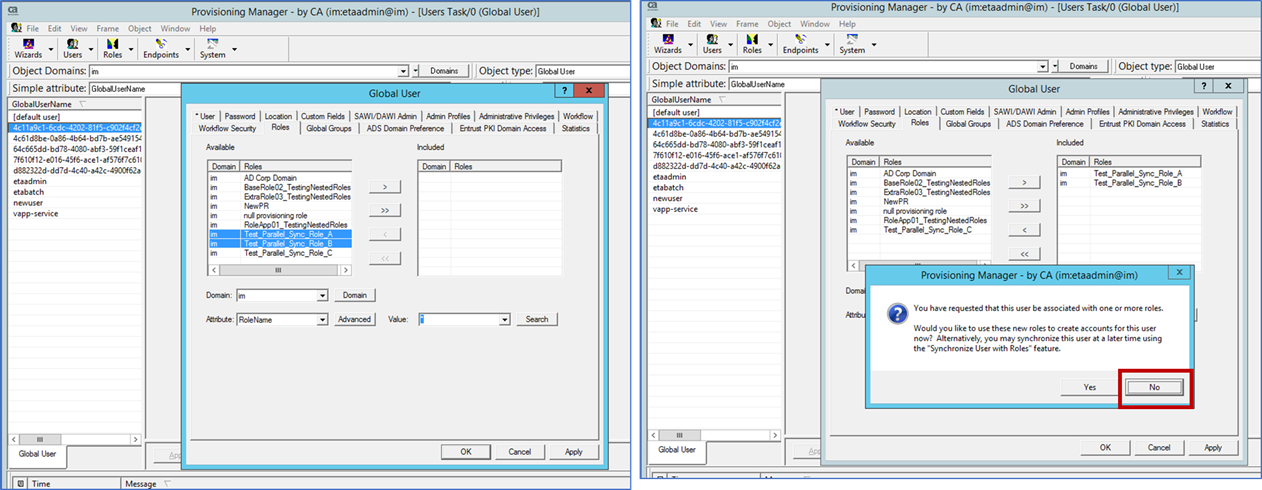
- As a pre-step, you may wish to assign working provisioning roles to a global user, but do not allow a sync operation in the IMPS GUI. This will allow you to identify if the process is working fine.
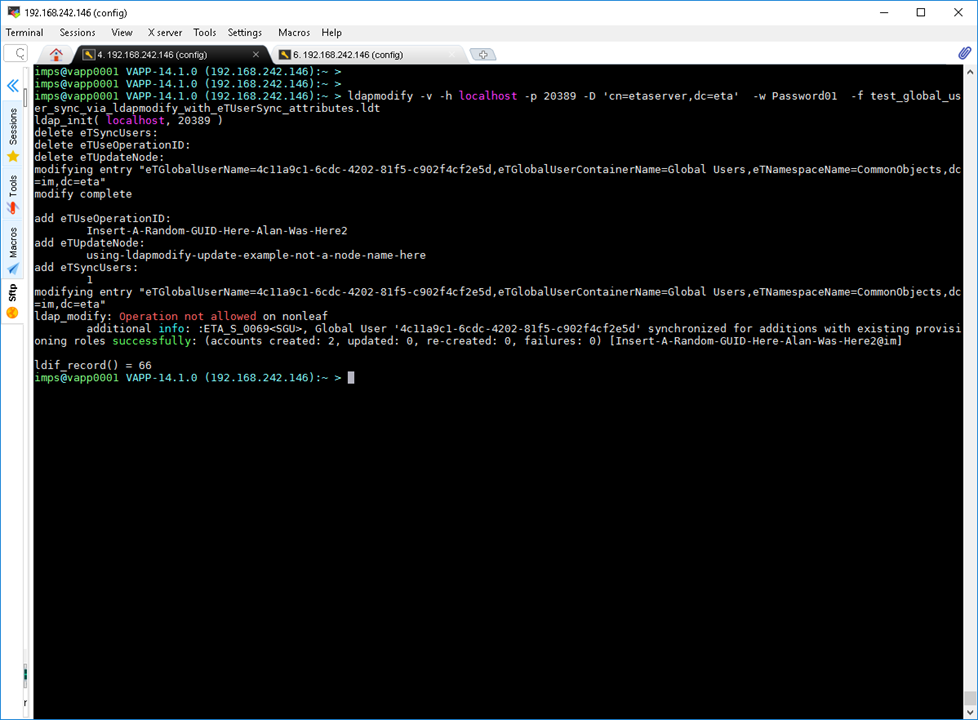
ldapmodify -v -h localhost -p 20389 -D 'cn=etaserver,dc=eta' -w Password01 -f test_global_user_sync_via_ldapmodify_with_eTUserSync_attributes.ldt
ldap_init( localhost, 20389 )
delete eTSyncUsers:
delete eTUseOperationID:
delete eTUpdateNode:
modifying entry "eTGlobalUserName=4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d,eTGlobalUserContainerName=Global Users,eTNamespaceName=CommonObjects,dc=im,dc=eta"
modify complete
add eTUseOperationID:
Insert-A-Random-GUID-Here-Alan-Was-Here2
add eTUpdateNode:
using-ldapmodify-update-example-not-a-node-name-here
add eTSyncUsers:
1
modifying entry "eTGlobalUserName=4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d,eTGlobalUserContainerName=Global Users,eTNamespaceName=CommonObjects,dc=im,dc=eta"
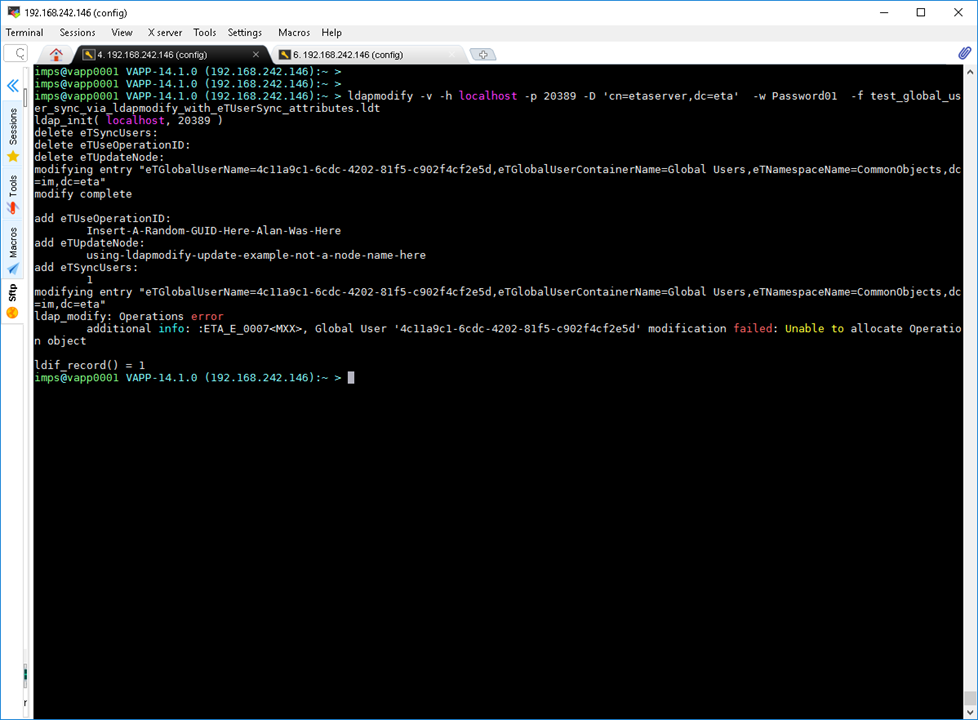
ldap_modify: Operation not allowed on nonleaf
additional info: :ETA_S_0069<SGU>, Global User '4c11a9c1-6cdc-4202-81f5-c902f4cf2e5d' synchronized for additions with existing provisioning roles successfully: (accounts created: 2, updated: 0, re-created: 0, failures: 0) [Insert-A-Random-GUID-Here-Alan-Was-Here2@im]
ldif_record() = 66
Additional examples below:
Pre-step: Attach provisioning roles to a global user, but do not sync the roles to the user (do not add).
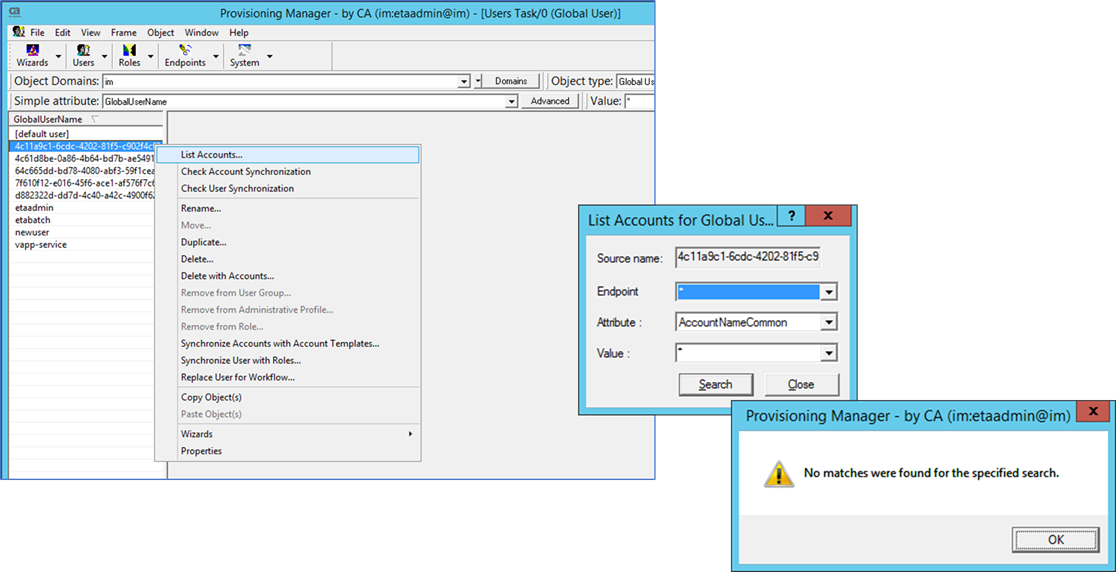
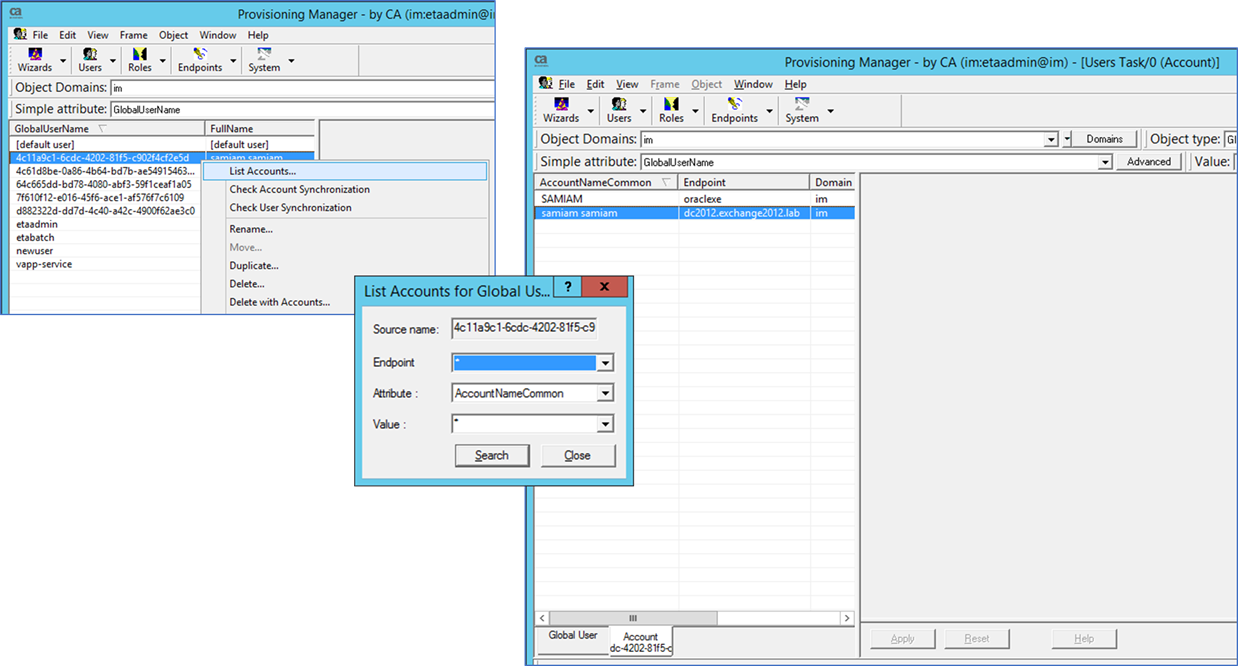
Confirm no endpoint accounts with List Accounts for the Global User
Example of input file:

Successful submission of ldap modify with sync on Global User with Roles.
- Note3: Ignore the standard ldapmod operations error/warning message; as it has no impact to the sync operation.
Using IMPS GUI, view that the newly created endpoint accounts have been created by the sync operation.
ERRORS:
Error seen if the Operational ID is NOT unique:
- Note2: The eTUseOperationID must be an unique string, e.g. GUID
I tested with a random text string to find out any limitation.
This value will be placed in the IMPD branch to be compared for uniqueness.
eTOperationID=XXXXX,eTOperationContainerName=Operations,eTNamespaceName=CommonObjects,dc=im,dc=etadb
This ID is maintained in the IMPD DSAs.
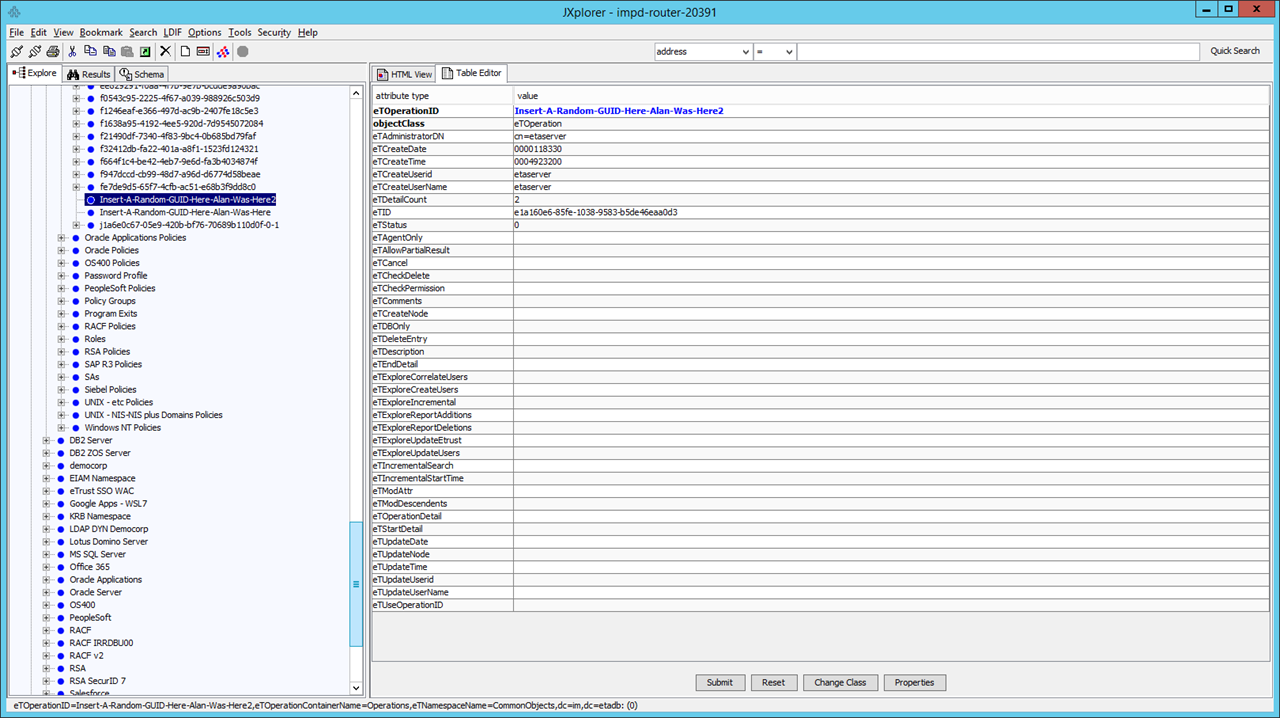
Not on the Global User record, even though it was modified there. The IMPS service will check, use and then move this entry.
Other Standard Provisioning Errors:
- Due to pre-existing account or missing password or native password quality check failed.
Cheers,
A.